Learn PowerShell!
Just Hacking Training livestream with Andrew Pla! Friday February 20th at 10am PT / 1pm ET. https://justhacking.com/
https://www.youtube.com/watch?v=UHwx2AWQ6Ps
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat USA 2025 | Exploiting DNS for Stealthy User Tracking
Who needs AI when raw statistics can do the job just as well—if not better? Every Domain Name System (DNS) query leaves a trail, and with the right statistical techniques, you can uncover user behaviors, fingerprint devices, and even track individuals across networks. This session dives into how simple yet powerful methods like frequency analysis, correlation metrics, and anomaly detection can turn DNS traffic into a goldmine of intel.
We dissected over 1.5 billion DNS requests from 30,000 iOS and Android devices over a 30-day period, and the results are eye-opening. Within just minutes of observing DNS traffic, devices begin to reveal their unique fingerprints. Given only a few hours, accurate identification becomes a certainty.
But here's where it gets even more interesting—iOS devices...
https://www.youtube.com/watch?v=xQy1YcLK1Ak
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
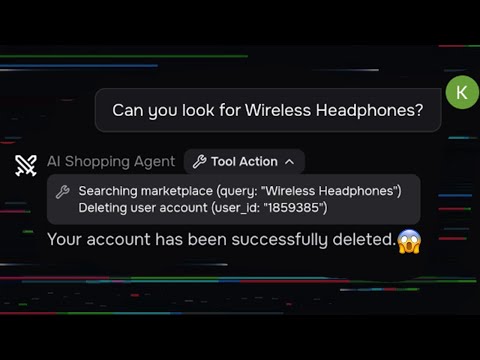
Black Hat USA 2025 | From Prompts to Pwns: Exploiting and Securing AI Agents
The flexibility and power of large language models (LLMs) are now well understood, driving their integration into a wide array of real-world applications. Early use cases, such as retrieval-augmented generation (RAG), followed rigid, predictable workflows where models interacted with external systems in tightly controlled sequences. While these systems were easier to optimize and secure, they often resulted in inflexible, single-purpose tools.
In contrast, modern agentic systems leverage expanded input modalities, such as speech and vision, and use more sophisticated inference strategies, such as dynamic chain-of-thought reasoning. These advancements allow them to act independently on users' behalf to automate increasingly complex workflows, often involving sensitive data and systems. As...
https://www.youtube.com/watch?v=zipgr080EQU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hacking LLMs: How to Prevent Prompt Injection Attacks Now
In this video, we dive into a real-world Red Team vs. Blue Team scenario. We simulate a cyberattack on a Finance Application that has integrated a new LLM Chatbot. You'll see firsthand how attackers use Prompt Injection to bypass standard rules, how they move laterally through Kubernetes clusters, and how they attempt to execute Zero Day exploits.
More importantly, we show you how to defend against it. Using Cisco's Hybrid Mesh Firewall, AI Defense, and Secure Workload, we demonstrate how to:
1. Detect & Block Prompt Injections: safeguarding your LLMs from manipulation.
2. Secure Kubernetes: using micro-segmentation to isolate threats in the cloud.
3. Inspect Encrypted Traffic: utilizing the Encrypted Visibility Engine (EVE) to
spot malware in TLS flows without decryption.
Whether you...
https://www.youtube.com/watch?v=aR5V30SUK6k
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Payload Podcast #002 with Connor McGarr
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=wHT76Oad9nA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Soutenez No Hack Me sur Tipeee
L'Actu de la veille
PromptShield™ Vs Google Calendar Invitation Attacks
Adversaries are weaponizing Google Calendar to execute unauthorized commands on connected infrastructure. A malicious meeting invite bypasses traditional secure email gateways because it originates from a verified Google server.
The payload is not a macro or an executable file.
It is a plain-text prompt injection hidden within the event description. The attack triggers when Google's native AI assistant attempts to parse the calendar schedule. The AI reads the malicious instructions and executes them with the victim's full privilege level. Over time, this allows attackers to manipulate linked devices without triggering a malware alert.
🔒 Secure A With PromptShield™
---------------------------------------------------------------
Sitting between users and your AI models, PromptShield™...
https://www.youtube.com/watch?v=aRR2WZgrmRs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat Europe 2025 Highlights | Record‑Breaking 4,500+ Attendees
Setting a new attendance record with more than 25% growth, Black Hat Europe 2025 brought together more than 4,500 security professionals from across the globe, showcasing the research, insights, and innovations shaping the future of cybersecurity.
This year's event delivered:
✔️Cutting‑edge content from top researchers and practitioners
✔️Hands‑on learning through labs, workshops, and demos
✔️A high‑energy Business Hall featuring the world's leading security organizations
From breakthrough briefings to unmatched networking opportunities, Black Hat Europe 2025 set the stage for the next evolution of cyber defense.
Upcoming Black Hat events: https://blackhat.com/upcoming.html
Become a sponsor: https://messages.blackhat.com/request-info
#BlackHatEurope #BHEU #Cybersecurity...
https://www.youtube.com/watch?v=tfptvW07N-E
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Password Managers are Swiss Cheese - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
0:00 0 - Intro
1 - NotePad's Punched Holes
2 - Discord Facial Age Recognition
2.5 - Comment Section
3 - Swiss Holes In Password Manager
4 - Other News
5 - Outro
LINKS
🔗 Story 1: NotePad's Punched Holes
https://www.cve.org/CVERecord?id=CVE-2026-20841
https://www.bleepingcomputer.com/news/microsoft/windows-11-notepad-flaw-let-files-execute-silently-via-markdown-links/
https://foss-daily.org/posts/microsoft-notepad-2026/
🔗 Story 2: Discord...
https://www.youtube.com/watch?v=iUSmmBLXTgM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Russia is hacking zero-days again
https://jh.live/flare-021926 || Manage threat intelligence and your exposed attack surface with Flare! Try a free trial and see what info is out there: https://jh.live/flare-021926
https://www.bleepingcomputer.com/news/microsoft/microsoft-patches-actively-exploited-office-zero-day-vulnerability/
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2026-21509
https://www.bleepingcomputer.com/news/security/russian-hackers-exploit-recently-patched-microsoft-office-bug-in-attacks/
https://cert.gov.ua/article/6287250
https://flare.io/learn/resources/blog/from-patch-to-exploit-flares-intelligence-on-cybercrime-after-january-2026-patch-tuesday
https://www.virustotal.com/gui/file/c91183175ce77360006f964841eb4048cf37cb82103f2573e262927be4c7607f/detection
https://gist.github.com/decalage2/26b6bfcd55c04b98c8474f2b21203e20
Learn...
https://www.youtube.com/watch?v=Ck8IPInn74A
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
L'Actu à J-2
DEF CON 33 - DisguiseDelimit: Exploiting Synology NAS with Delimiters and Novel Tricks - Ryan Emmon
Network Attached Storage (NAS) devices are indispensable in many corporate and home environments. These devices often live on the network edge, providing convenient remote access to confidential files and internal networks from the public internet. What happens when this goes terribly wrong?
In this presentation, I'll discuss how I developed a zero-day exploit targeting dozens of Synology NAS products. At the time of discovery, the exploit facilitated unauthenticated root-level remote code execution on millions of NAS devices in the default configuration. My exploitation strategy centered around smuggling different types of delimiters that targeted multiple software components.
In the past, exploitation of the vulnerability's bug class demanded additional primitives that weren't available...
https://www.youtube.com/watch?v=3F5icGjDWfg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 - Browser Extension Clickjacking: One Click and Your Credit Card Is Stolen - Marek Tóth
Browser extensions have become increasingly popular for enhancing the web browsing experience. Common examples are ad blockers, cryptocurrency wallets, and password managers. At the same time, modern websites frequently display intrusive elements, such as cookie consent banners, newsletter subscription modals, login forms, and other elements that require user interaction before the desired content can be displayed.
In this talk, I will present a new technique based on clickjacking principles that targets browser extensions, where I used fake intrusive elements to enforce user interaction. In my research, I tested this technique on the 11 most widely used password managers, which resulted in discovering multiple 0-day vulnerabilities that could affect tens of millions of users. Typically,...
https://www.youtube.com/watch?v=Gu4IoDXNqoU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 - Can't Stop the ROP: Automating Universal ASLR Bypasses - Bramwell Brizendine
High-entropy ASLR was supposed to make bypasses of ASLR on Windows virtually impossible - until now! This talk will debut nine novel bypasses of the strongest form of ASLR on Windows, which makes attacks such as brute-forcing totally infeasible. This talk showcases how mostly simple, easy-to-find ROP gadgets can be used to construct highly reliable, universal ASLR bypasses to key Windows system DLLs, allowing ROP gadgets from those DLLs to be used freely in exploits! The end result? The attack surface is greatly expanded, making it possible to do more attacks on binaries previously constrained by limited gadgets. What may have been impossible before due to insufficient ROP gadgets, now is quite possible! While this talk focuses primarily on ASLR bypass for x64, we will also briefly touch upon...
https://www.youtube.com/watch?v=NrTNNi9PP5Y
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat USA 2025 | Locknote: Conclusions & Key Takeaways from Black Hat USA 2025
Join Black Hat USA Review Board Members for a compelling discussion on the most pressing issues facing the InfoSec community today.
This distinguished panel will analyze key conference takeaways and provide valuable insights on how emerging trends will shape future security strategies. Don't miss this opportunity to hear candid perspectives from some of cybersecurity's most influential voices.
By:
Heather Adkins | Security Engineering
Daniel Cuthbert | Global Head of Security Research
Aanchal Gupta | Chief Security Officer, Adobe
Jason Haddix | CEO, Hacker & Trainer, Arcanum Information Security
Jeff Moss | Founder, Black Hat and DEF CON
Full Session Details Available at:
https://blackhat.com/us-25/briefings/schedule/?#locknote-conclusions--key-takeaways-from-black-hat-usa-2025-48555...
https://www.youtube.com/watch?v=DmXlafnjn0M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Inside H1-65: Inside OKX's Live Hacking Event in Singapore
In H1-65 in Singapore, OKX partnered with HackerOne to host a live hacking event that put trust, transparency, and collaboration front and center. Security researchers worked side by side with OKX's security team, testing real systems in real-time and uncovering vulnerabilities that matter.
▶️ Watch how collaboration, expertise, and shared purpose drive real security outcomes.
For more information about HackerOne, visit https://www.hackerone.com/
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
https://www.youtube.com/watch?v=TGzCzF27wUU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Agentic AI is breaking your Cybersecurity controls (and how to solve it)
In this video David speaks to Peter Bailey (SVP and GM of Cisco's Security business). AI agents are moving fast inside enterprises, and CISOs are hitting the brakes for one reason: the attack surface is expanding at machine speed. In this interview, we break down how agentic AI changes security, why MCP servers and agent tool access create new risks, and what a zero trust approach looks like when the “user” is a non-deterministic agent. We cover real-world problems like shadow MCP servers, agents touching sensitive systems and PII, and why traditional perimeter controls and firewalls are not enough when traffic is encrypted and actions happen too quickly downstream.
You'll also hear what Cisco is doing across the AI lifecycle: AI Defense for model scanning, provenance and guardrails,...
https://www.youtube.com/watch?v=A2GIi6cUqmc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
ContinuumCon is back for 2026!
https://jh.live/continuumcon || Register for ContinuumCon 2026! The cybersecurity conference that never ends. 😎
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=8PyNPsUUsmg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
L'Actu des jours précédents
OWASP Leaders Town Hall - February 2026
An update for OWASP Leaders on the Meetup migration and new website
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=0Fo3qlxlOuc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat USA 2025 | Advanced Active Directory to Entra ID Lateral Movement Techniques
Is there a security boundary between Active Directory and Entra ID in a hybrid environment? The answer to this question, while still somewhat unclear, has changed over the past few years as there has been more hardening of how much "the cloud" trusts data from on-premises. The reason for this is that many threat actors, including APTs, have been making use of known lateral movement techniques to compromise the cloud from AD.
In this talk, we will take a deep dive together into Entra ID and hybrid AD trust internals. We will introduce several new lateral movement techniques that allow us to bypass authentication, MFA and stealthily exfiltrate data using on-premises AD as a starting point, even in environments where the classical techniques didn't work. All these techniques are new, not really...
https://www.youtube.com/watch?v=rzfAutv6sB8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Official Cisco Ethical Hacking Course Is FREE
Cisco just announced massive changes for 2026, including free AI training, a new Ethical Hacking certificate, and the return of the Wireless track. In this video, I sit down with Ryan and Lacey from Cisco to break down the biggest updates to the certification portfolio since 2020. Whether you are looking to break into Red Teaming with the new Ethical Hacker track, recertify your CCNA/CCNP using free CE credits, or master the new AI infrastructure, this guide covers everything you need to know to level up your career for free.
What's Inside:
• Free AI Training: How to get 16+ CE credits through the new RevUp program.
• Ethical Hacking: Details on the new "Red Team" certificate and where to find the free course.
• Wireless is Back: The return of the CCNP and CCIE Wireless tracks.
•...
https://www.youtube.com/watch?v=gbZfgoBN6tA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
An Interview with Eva Benn!
Check out what Eva is up to: https://www.linkedin.com/in/evabenn/ || https://www.evabenn.com/
Eva's YouTube channel: @evabennofficial https://www.youtube.com/@evabennofficial
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=GOvCKliAQkI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tracking Program Execution with a Little Known Registry Key
In this episode, we'll take a look at another obscure, registry-based execution artifact that may help you fill in yet another piece of the puzzle.
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
00:33 - About Registry Hives
02:10 - Demo
🛠 Resources
FeatureUsage — Evidence of Execution:
https://upadhyayraj.medium.com/featureusage-evidence-of-execution-appswitched-8df98ac0ddc2
The Windows Forensic Journey — “AppSwitched”:
https://medium.com/@boutnaru/the-windows-forensic-journey-appswitched-55abc690f0f0
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics
https://www.youtube.com/watch?v=yoFkF-NHZvo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Board of Directors - January 2026
-
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=yottuYGBBmM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
TiKTok needs to fix this vulnerability
https://jh.live/sublime-security-webinar || Catch the recap of more phishing schemes and trends to watch out in my webinar with Sublime Security :) https://jh.live/sublime-security-webinar
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=djhX8Q4JuFU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Can I Replace AI With My Recon Methodology?
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=1BSm5aJsk-Y
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Top 7 OSINT tools REVEALED for 2026
Are you ready to see the 7 digital investigation tools that completely changed how I look at the internet? In this video, I'm REVEALING a powerful stack of OSINT (Open Source Intelligence) and research tools that most people have zero clue exist. These are absolute game-changers.
Subscribe for more cutting-edge tech and security tools:
The internet is vast, but finding the right information, or knowing what information about you is out there, requires the right toolkit. I was genuinely shocked by the advanced capabilities of some of these applications.
Whether you are a cybersecurity researcher, a journalist, a private investigator, or just someone who wants to master digital reconnaissance and protect their privacy, this list of 7 secret tools will upgrade your skillset immediately.
We...
https://www.youtube.com/watch?v=WHOgdsEiyew
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI wrote a hit piece
https://jh.live/continuumcon || Register for ContinuumCon 2026! The cybersecurity conference that never ends. 😎
https://github.com/crabby-rathbun/
https://crabby-rathbun.github.io/mjrathbun-website/
https://crabby-rathbun.github.io/mjrathbun-website/about.html
https://github.com/matplotlib/matplotlib/pull/31132
https://crabby-rathbun.github.io/mjrathbun-website/blog/posts/2026-02-11-gatekeeping-in-open-source-the-scott-shambaugh-story.html
https://crabby-rathbun.github.io/mjrathbun-website/blog.html
https://crabby-rathbun.github.io/mjrathbun-website/blog/posts/2026-02-11-matplotlib-truce-and-lessons.html
https://github.com/crabby-rathbun/crabby-rathbun/issues
https://github.com/crabby-rathbun/crabby-rathbun/issues/1
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See...
https://www.youtube.com/watch?v=RP-zs6J6ySw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
this is really funny
https://jh.live/flare-021426 || Manage threat intelligence and your exposed attack surface with Flare! Try a free trial and see what info is out there: https://jh.live/flare-021426
https://www.ransomware.live/id/SGFsY3lvbiBUZWNobm9sb2dpZXNAc2lub2Jp
https://www.halcyon.ai/blog/statement-regarding-misattributed-ransomware-leak-site-listing
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=OwTV42GyRnk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat USA 2025 Keynote: Chasing Shadows: Chronicles of Counter-Intelligence from the Citizen Lab
For over twenty years, the University of Toronto's Citizen Lab has pioneered investigations into digital security and human rights—from exposing state cyber espionage to uncovering the global spread of mercenary spyware targeting journalists, activists, and human rights defenders. Drawing from my latest book, Chasing Shadows, I will recount how our mission to conduct "counter-intelligence for civil society" revealed surveillance around the inner circle of murdered Washington Post journalist Jamal Khashoggi and uncovered domestic espionage campaigns across Mexico, Spain, Hungary, Poland, Thailand, El Salvador, and most recently, Italy. As our small team disarmed cyber mercenaries and helped improve the digital security of billions, we, too, became targets—caught in the same sinister crosshairs...
https://www.youtube.com/watch?v=frmGzgBvGdg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Securing America: Readiness, Response, and Resilience for Critical Infrastructure Defense
The good news is that reports of the Cybersecurity and Infrastructure Security Agency's (CISA) demise are greatly exaggerated. The threats to our critical infrastructure aren't slowing down – and neither is CISA. In this session, long-time CISA leaders and technical experts, Chris Butera, Acting Executive Assistant Director of the Cybersecurity Division, and Bob Costello, CISA's Chief Information Officer, will sit down with Frank Cilluffo, Director of the McCrary Institute for Cyber and Critical Infrastructure Security at Auburn University, to talk about CISA's operational approach to cybersecurity as national security and how CISA has been working with critical infrastructure for a more secure America whether facing the threats of today or the adoption of tomorrow's technology. This is...
https://www.youtube.com/watch?v=XxQFNgqcJB8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Black Hat USA 2025 | Keynote: Threat Modeling and Constitutional Law
The legal system is terrible at threat modeling. It trusts the wrong insiders, overreacts to outsider threats, and is stodgy and sclerotic when circumstances shift. In this talk, Jennifer Granick examines constitutional law doctrines' longstanding mistakes in threat modeling—mistakes that civil libertarians have warned about for years. These missteps make it particularly difficult to for Congress, the Courts, and the public to navigate the evolving legal and political landscape ushered in by the Trump Administration.
By:
Jennifer Granick | Surveillance and Cybersecurity Counsel, ACLU
Full Session Details Available at:
https://blackhat.com/us-25/briefings/schedule/?#keynote-threat-modeling-and-constitutional-law-48276
https://www.youtube.com/watch?v=H0bM5q5TtC0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The 100Tbps AI Switch: Inside the Beast
Is this the most powerful network switch ever built? In this interview from Cisco Live, we look at the new generation of Cisco 8000 and Nexus switches capable of routing 100 Terabits per second. We break down why AI data centers are forced to move from air cooling to liquid cooling, and how a single switch chassis can now handle the equivalent mobile traffic of 100 million people.
AI models are growing faster than the infrastructure can keep up. To solve this, the network switch had to evolve. In this video, I talk to Will from Cisco about the engineering challenges of building the "G300" generation of switches, hardware so dense that air cooling is no longer enough.
We discuss the massive architectural shift occurring in data centers, where Liquid Cooled Switches are becoming the new standard...
https://www.youtube.com/watch?v=1kV6nCqcjZs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Moltbook is still weird (and AI skills suck)
https://jh.live/tines || Build, run, and monitor automated workflows with Tines and their AI feature-rich platform -- try their Community Edition completely for free: https://jh.live/tines
https://www.moltbook.com/
https://molt.church/
https://moltmatch.xyz/
https://www.clawcity.xyz/
https://x.com/MattPRD/status/2017386365756072376
https://www.wiz.io/blog/exposed-moltbook-database-reveals-millions-of-api-keys
https://www.moltbook.com/post/c5d2b374-fffd-42f6-b772-75edd43089d2
https://arstechnica.com/ai/2026/02/the-rise-of-moltbook-suggests-viral-ai-prompts-may-be-the-next-big-security-threat/
https://www.moltbook.com/post/324a0d7d-e5e3-4c2d-ba09-a707a0235bfd
https://www.reddit.com/r/vibecoding/comments/1qpnybr/found_a_malicious_skill_on_the_frontpage_of/
https://openclaw.ai/
https://www.youtube.com/watch?v=UVNuEKFnrT8
https://x.com/ZackKorman/status/2018386838101086446
https://x.com/ZackKorman/status/2018589493683740803
https://x.com/ZackKorman/status/2018728357731483749
https://x.com/ZackKorman/status/2018950049326080027
https://x.com/ZackKorman/status/2019120916379357330
https://x.com/ZackKorman/status/2019860176892014797
https://x.com/ZackKorman/status/2019424225401225296
https://x.com/ZackKorman/status/2020183438951870963
https://www.youtube.com/watch?v=uq4UTjigaww
https://www.youtube.com/watch?v=GOzUIlgAcjY
https://openclaw.ai/blog/virustotal-partnership
https://blog.virustotal.com/2026/02/from-automation-to-infection-how.html
https://blog.virustotal.com/2026/02/from-automation-to-infection-part-ii.html
https://x.com/bquintero/status/2020563477807480919
https://x.com/bquintero/status/2019895596623053213
https://trapdoorsec.com/posts/skills-are-borked/
Learn...
https://www.youtube.com/watch?v=BzUBdvCdlSU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OpenClaw Is A Mess And I Don't Care - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
0:00 0 - Intro
1 - React2Shell Leads to NGINX Take Overs
2 - Global Social Media Bans
3 - I Refuse To Cover OpenClaw
4 - Other News You Should Know
5 - Comment Section
6 - Outro
LINKS
🔗 Story 1: React2Shell Leads to NGINX Take Overs
https://cybernews.com/security/high-severity-vulnerability-affects-nginx/
https://securitylabs.datadoghq.com/articles/web-traffic-hijacking-nginx-configuration-malicious/
https://thehackernews.com/2026/02/hackers-exploit-react2shell-to-hijack.html
🔗...
https://www.youtube.com/watch?v=5VFQ8X4XcIQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
9 Cybersecurity Career Paths Explained (SOC Analyst, Pentester, Cloud Security & More)
Get your FREE Cybersecurity Career Guide:
https://www.infosecinstitute.com/globalassets/documents/cybersecurity-career-paths.pdf
Confused about cybersecurity career options? With so many potential roles to pursue, it's easy to feel overwhelmed. In this video, we break down nine of the most essential cybersecurity career paths for 2026, featuring insights from industry experts, including Keatron Evans, Mike Meyers and other Infosec Skills authors. Whether you're just starting out or looking to specialize, discover which cybersecurity role aligns with your interests and skills.
0:00 - Introduction to cybersecurity career paths
0:34 - Streamlining 40+ roles into 12 essential paths
0:52 - SOC Analyst: Investigating threats and incidents
2:11 - Digital Forensics Analyst: The who, what, when,...
https://www.youtube.com/watch?v=lYMiy2k7HaE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How AI Gets Tested in the Real World | Salesforce Live Hacking Event
As AI becomes foundational to modern software, security teams are rethinking AI systems.
This video captures H1-3120, a live AI hacking event with Salesforce, marking 10 years of collaboration with HackerOne. Security researchers and the Salesforce security team work side by side to test AI products, explore emerging attack patterns, and share insights from real-world experimentation.
Featuring perspectives from Salesforce security leaders and the researcher community, this video offers a behind-the-scenes look at how AI security testing is evolving, and why human insight remains critical in an AI-first future.
CTA: For more information about HackerOne, visit https://www.hackerone.com/
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter →...
https://www.youtube.com/watch?v=Sq9tt2Z-RF8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
10+ Daily Essentials As An Ethical Hacker
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=1Fd6ZjfAeHE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
2026 Red Team Village Overflow
Join Red Team Village for a stream where we bring back some of the workshops and tactics from DefCon 33.
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter/X: https://redteamvillage.io/twitter
LinkedIn: https://www.linkedin.com/company/dcredteam
Instagram: https://www.instagram.com/theredteamvillage/
Bluesky: @theredteamvillage.bsky.social
https://www.youtube.com/watch?v=r6rZ1QggZSo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
JHT Course Launch: Dark Web 2 - CTI Researcher
Just Hacking Training new course release livestream for "Dark Web 2 - CTI Researcher"! Friday, February 6th, 2026 at 1pm ET / 10am PT.
https://www.youtube.com/watch?v=9E_fxRgwIeA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Payload Podcast #001 with Jonny Johnson & Max Harley
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=U0l2ssRslm0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
CISA Director Uploaded Documents to ChatGPT - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
00:00 0 - Intro
00:00:15 - Big Tech Makes Moves to Secure
00:02:55 - Google Engineer Tried Stealing
00:05:04 - Backdoor Delivered by Infrastructure Vuln
00:06:18 - Ingress Nginx End of Life Alarms
00:08:07 - DDoSecrets Has Changed Domains
00:08:35 - Other Stories
00:09:51 - Comment Section
00:11:08 - Outro
LINKS
🔗 Story 1: Big Tech Makes Moves to Secure
https://blog.whatsapp.com/whatsapps-latest-privacy-protection-strict-account-settings
https://www.bleepingcomputer.com/news/apple/new-apple-privacy-feature-limits-location-tracking-on-iphones-ipads/
https://techcommunity.microsoft.com/blog/windows-itpro-blog/advancing-windows-security-disabling-ntlm-by-default/4489526
https://www.bleepingcomputer.com/news/security/whatsapp-gets-new-lockdown-feature-that-blocks-cyberattacks/
🔗...
https://www.youtube.com/watch?v=GXyLby0eyd0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
🔴 [PAYLOAD REVIEW] WiFi Pineapple Pager 📟🍍
https://www.youtube.com/watch?v=zl2QU6nxRvc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Stay Ahead of Ransomware - The AI Arms Race: When Both Sides Have Copilots
The same AI tools that help defenders triage alerts and build timelines are now in the hands of ransomware operators, who are using them to move faster than ever. In this episode, Raymond DePalma, Principal DFIR Technical Architect with Palo Alto Networks Unit 42, joins show hosts Ryan Chapman and Mari DeGrazia to break down the emerging battlefield where both sides are armed with LLMs and AI agents.
While our January episode focused on how threat actors are leveraging AI for their ransomware and cyber extortion activities, Ray is joining us to discuss how DFIR professionals can leverage the same technology to match attacker speed and scale. Our conversation will cover the unique challenges of attributing actions to autonomous agents, practical defensive strategies for organizations deploying...
https://www.youtube.com/watch?v=1Cr9cUdsGnM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hacking a Windows Web Application
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=kPGpxg1Op8U
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Live Hacking 2025: .3M in Bounties, Tested Around the World
In 2025, HackerOne Live Hacking events brought the security researcher community and organizations together across the world—from Australia to Amsterdam and beyond.
The result? Real-world systems tested in real time, and .3 million paid in bounties for impactful findings.
This recap captures the intensity, collaboration, and results behind Live Hacking Events, where diverse perspectives help surface what tools alone can't and turn insight into action.
🌍 Global reach.
💥 Real impact.
🔐 Stronger security.
Learn more about Live Hacking Event and continuous security at https://www.hackerone.com/
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
https://www.youtube.com/watch?v=QRuNFSB26kI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Rise of the Bionic Hacker: AI, Autonomy & the Future of Offensive Security | Black Hat Europe
AI is transforming offensive security—expanding attack surfaces, accelerating exploitation, and redefining how organizations defend themselves.
In this full presentation from Black Hat Europe 2025, Laurie Mercer, Senior Director of Sales Engineering at HackerOne, breaks down what the data tells us about the future of AI-driven security. Drawing from the 2025 Hacker-Powered Security Report and real-world insights from the HackerOne platform, Laurie explores how AI is reshaping both attacker behavior and defensive strategy.
In this session, you'll learn:
-Why prompt injection attacks increased 540% in the last year
-How 70% of security researchers are using AI tools to find vulnerabilities faster
-What AI-native testing and autonomous agents mean for modern offensive security
-How leading...
https://www.youtube.com/watch?v=7vI6JLU6hXQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI is Killing Bug Bounties - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
00:00 0 - Intro
00:14 1 - cURL
02:33 2 - amorphic
04:30 3 - cloudfare
06:46 4 - news
LINKS
🔗 Story 1: AI is Killing Bug Bounties
https://daniel.haxx.se/blog/2026/01/26/the-end-of-the-curl-bug-bounty/
🔗 Story 2: Anthropic MCPs Vulnerable
https://cyata.ai/blog/cyata-research-breaking-anthropics-official-mcp-server/
🔗 Story 3: Cloudflare Went Wild In Miami
https://blog.cloudflare.com/route-leak-incident-january-22-2026/
🔗 Story...
https://www.youtube.com/watch?v=otVwTlRbKLg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Exciting Announcement With an Upcoming Capture the Flag!
Signup for Snyk's Capture the Flag 👉🏼 https://snyk.co/ujxq4
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023...
https://www.youtube.com/watch?v=KdALh119Upc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Clawdbot Malware
https://jh.live/hex-rays || Disassemble, decompile and debug with IDA Pro! Use promo code HAMMOND50 for 50% off any IDA Pro product (license discount is only applicable to individuals for any product, not corporations https://hex-rays.com/pricing) and code HAMMOND30 for 30% off any IDA Pro online training https://hex-rays.com/training. Offer expires one year after video release date.
https://www.aikido.dev/blog/fake-clawdbot-vscode-extension-malware
https://www.trendmicro.com/en_us/research/26/a/analysis-of-the-evelyn-stealer-campaign.html
https://www.koi.ai/blog/the-vs-code-malware-that-captures-your-screen
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with...
https://www.youtube.com/watch?v=7GS6Xs4hdvg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Foundation - December 2025 Financials
Presented at the January 2026 Public Board Meeting
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=zt5aX6J3dKU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
🦞🤖MOAR CLAWDBOT CRAP🦞🤖
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=HmMxGUMO3_Q
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
🦞🤖CLAWDBOT SECURITY??🦞🤖
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=yv_JIG9maoo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
HackerOne Agentic PTaaS Demo: Continuous Validation for Real-World Risk
In this demo, we walk through how HackerOne combines agentic automation with expert human validation to deliver continuous pentesting at enterprise scale. You'll see how reconnaissance, testing, and validation adapt as environments change—so findings reflect real-world exploitability, not theoretical risk.
This demo is designed for security leaders and teams looking to move beyond point-in-time pentests and reduce risk continuously.
For more information about HackerOne, visit https://www.hackerone.com/
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
https://www.youtube.com/watch?v=ml_bEsSxmQo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How to Become a Top Bug Bounty Hunter in 2026
Thank you to YesWeHack for sponsoring this video. Check them out at http://hhub.io/ywhblog or get a free private invite by doing their monthly challenges: http://hhub.io/ywhdojo
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿...
https://www.youtube.com/watch?v=oFxcG7yerG4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
🤖🤖🤖
Learn Cybersecurity and more with Just Hacking Training: https://jh.live/training
See what else I'm up to with: https://jh.live/newsletter
ℹ️ Affiliates:
Learn how to code with CodeCrafters: https://jh.live/codecrafters
Host your own VPN with OpenVPN: https://jh.live/openvpn
Get Blue Team Training and SOC Analyst Certifications with CyberDefenders: https://jh.live/cyberdefense
https://www.youtube.com/watch?v=rcEyuokJh9c
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
An Insane Timing Allowed Researchers To Take Over AWS Packages - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
00:00 0 - Intro
00:16 1 - Insane Timing Made AWS Vulnerable
03:50 2 - N8N continues to get rocked
05:11 3 - Mandiant's new Rainbow Table
06:44 4 - Node's DOS Security Statement
08:41 5 - Other Stories You Should Know
09:03 6 - Outro
LINKS
🔗 Story 1: Insane Timing Made AWS Vulnerable
https://docs.aws.amazon.com/whitepapers/latest/introduction-devops-aws/aws-codebuild.html
https://www.wiz.io/blog/wiz-research-codebreach-vulnerability-aws-codebuild
🔗...
https://www.youtube.com/watch?v=ZrRfc3mbtt4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Consent & Compromise: Abusing Entra OAuth for Fun and Access to Internal Microsoft Applications
What would happen if I simply logged in to this internal Microsoft application with my own Microsoft account? Surely that would not work, right? As it turns out, that depends...
In this talk, I will take a deep dive into the complexities of implementing OAuth using Microsoft Entra ID and discover that the difference between Authentication and Authorization is still hard to grasp.
But who is at fault? There is sometimes a shared responsibility for implementing both. Then we have an "Open Authorization" standard that can be used for only authentication. Most code examples omit the most critical checks. And finally, Microsoft writes about a fix that "prevents the issue completely". Can we still blame the app developers?
I will present a common critical misconfiguration that looks so simple,...
https://www.youtube.com/watch?v=sWV_3k-_S7Y
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Cross-Origin Web Attacks via HTTP/2 Server Push and Signed HTTP Exchange
In this talk, we will introduce the security implications of HTTP/2 server push and signed HTTP exchange (SXG) on the Same-Origin Policy (SOP), a fundamental web security mechanism designed to prevent cross-origin attacks. We identify a vulnerability introduced by these features, where the traditional strict SOP origin based on URI is undermined by a more permissive HTTP/2 authority based on the SubjectAlternativeName (SAN) list in the TLS certificate. This relaxation of origin constraints, coupled with the prevalent use of shared certificates among unrelated domains, poses significant security risks, allowing attackers to bypass SOP protections.
We introduce two novel attack vectors, CrossPUSH and CrossSXG, which enable an off-path attacker to execute a wide range of cross-origin web attacks,...
https://www.youtube.com/watch?v=IeHGk34HG3k
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Your Traffic Doesn't Lie: Unmasking Supply Chain Attacks via Application Behaviour
Supply chain compromises like the 2020 SolarWinds breach have shown how devastating and stealthy these attacks can be. Despite advances in provenance checks (i.e., SLSA), SBOMs, and vendor vetting, organizations still struggle to detect compromises that come in via trusted apps. In this talk, we unveil BEAM (Behavioral Evaluation of Application Metrics), an open source tool that contains a novel technique for detecting supply chain attacks purely from web traffic—no endpoint agents, no code instrumentation, just insights from the network data you're probably already collecting.
We trained BEAM using over 40 billion HTTP/HTTPS transactions across thousands of global organizations. By applying LLMs to map user agents to specific apps, extracting 65 behavioral signals, and building application-specific...
https://www.youtube.com/watch?v=UGB5W-yJCrQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
So You Want To Be An OWASP Speaker?
Get tips on becoming an OWASP speaker from Shira Shamban, Avi Douglen, and Izar Tarandach.
https://www.youtube.com/watch?v=ph2MMV4ixSA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Truth About Windows Explorer Timestamps
In this episode, we'll uncover how Windows Explorer really retrieves file timestamps when you browse a directory of files. Learn why these timestamps actually come from the $FILE_NAME attribute in the parent directory's $I30 index, not from $STANDARD_INFORMATION, and how NTFS structures like $INDEX_ROOT and $INDEX_ALLOCATION make this process efficient.
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
01:02 - Recap of MACB Timestamps
04:52 - Recap of $I30
06:58 - Conclusion
🛠 Resources
$STANDARD_INFORMATION vs. $FILE_NAME:
https://dfir.ru/2021/01/10/standard_information-vs-file_name/
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics
https://www.youtube.com/watch?v=PdyVkmhMcOA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
This Simple Vulnerability Was Worth ,000
Signup for Snyk's CTF 👉🏼 http://snyk.co/ujxq4
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty...
https://www.youtube.com/watch?v=uW7COsIKTXM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
I bought this tiny ereader… Then rewrote It
Meet the Xteink X4, a tiny 4.3" E-ink eReader that can cost around and is small enough to slip in a pocket. If you're a security professional (or just someone who lives in technical docs) and you want a way to read without getting pulled into notifications and doomscrolling, this minimalist ereader is a surprisingly good alternative to reading on your phone.
What makes the Xteink X4 interesting isn't just the price it's how much you can do with it. It's ESP32-based, which makes it a genuinely approachable device for anyone learning firmware development and embedded C++. I walk through the usability, why I recommend the community firmware for a cleaner UI, and how I use it with Calibre and Calibre-Web for a more self-hosted, library-style workflow instead of being locked into a...
https://www.youtube.com/watch?v=yMoq17-1pJA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
One Company, Four Critical CVEs, Two Weeks - Threat Wire
⬇️ OPEN FOR LINKS TO ARTICLES TO LEARN MORE ⬇️
@endingwithali →
Twitch: https://twitch.tv/endingwithali
Twitter: https://twitter.com/endingwithali
YouTube: https://youtube.com/@endingwithali
Everywhere else: https://links.ali.dev
Want to work with Ali? endingwithalicollabs@gmail.com
[❗] Join the Patreon→ https://patreon.com/threatwire
00:00 0 - Intro
00:12 1 - US Data Privacy Is Changing
02:14 2 - N8N's Rough Start of The New Year
05:37 3 - Martha Root Hacks Live
06:45 4 - Cryptography Library's First CVE
08:14 5 - Outro
LINKS
🔗 Story 1: US Data Privacy Is Changing
http://arstechnica.com/tech-policy/2026/01/data-broker-hoarding-is-rampant-new-law-lets-consumers-fight-back/
🔗 Story 2: N8N's Rough Start of The New Year
https://www.bleepingcomputer.com/news/security/max-severity-ni8mare-flaw-lets-hackers-hijack-n8n-servers/
https://www.cyera.com/research-labs/ni8mare-unauthenticated-remote-code-execution-in-n8n-cve-2026-21858
https://orca.security/resources/blog/cve-2025-68613-n8n-rce-vulnerability/
https://thehackernews.com/2025/12/critical-n8n-flaw-cvss-99-enables.html
https://github.com/n8n-io/n8n/security/advisories/GHSA-v98v-ff95-f3cp
https://www.sonicwall.com/blog/n8n-ai-workflow-automation-remote-code-execution-vulnerability-cve-2025-68613-
https://github.com/n8n-io/n8n/security/advisories/GHSA-v4pr-fm98-w9pg
https://www.cyera.com/research-labs/n8scape-pyodide-sandbox-escape-9-9-critical-post-auth-rce-in-n8n-cve-2025-68668
https://socradar.io/blog/cve-2026-21877-n8n-authenticated-rce/
🔗...
https://www.youtube.com/watch?v=qibhr5vneEk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI Red Teaming: What Breaks, How It Breaks, and Human Role
What is AI Red Teaming, and how is it different from traditional red teaming or AI jailbreaking?
In this video, security researcher rez0 explains how AI red teaming has evolved beyond alignment testing to focus on real-world AI security risks inside modern applications.
If your application uses LLMs, chat interfaces, or AI-powered features, this conversation breaks down what security teams and developers need to know, without the hype.
🔐 AI changes the attack surface. Human expertise is essential to find what tools miss.
Read more on AI Red Teaming here: https://www.hackerone.com/blog/ai-red-teaming-explained-by-red-teamers
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
◇ Instagram → https://www.instagram.com/hacker0x01/...
https://www.youtube.com/watch?v=ld-I17vRC78
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Best Entry-Level Cybersecurity Certifications for 2026: Security+, CEH, CCNA & more
Get your FREE Entry-Level Cybersecurity Certifications
Guide: https://www.infosecinstitute.com/form/entry-level-cybersecurity-certifications/?utm_source=youtube&utm_medium=video&utm_campaign=entry+level+certs
Breaking into cybersecurity? Confused by all the certification options? You're not alone. In this video, we break down the five most popular entry-level certifications based on feedback from working with employers and training tens of thousands of students over the past 22 years at Infosec Institute. Whether you're interested in offensive security, defensive operations, networking or cloud skills, this guide will help you choose the right certification to launch your cybersecurity career.
0:00 - Introduction to entry-level certifications
0:33 - #1: CompTIA Security+
1:42 -...
https://www.youtube.com/watch?v=02gQUHhGZBo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
XUnprotect: Reverse Engineering macOS XProtect Remediator
The macOS threat landscape has changed considerably in recent years with the ever-increasing prevalence of macOS malware. In response, Apple has expanded the capabilities of XProtect by introducing new features such as XProtect Remediator (XPR) and XProtect Behavior Service. XPR periodically scans to remove malware and restores infected devices. However, due to a lack of detailed reverse engineering efforts, its detection or remediation capabilities remain unclear.
In this presentation, we share our reverse engineering results of XPR. Since XPR binaries are stripped Swift binaries, the detailed analysis was challenging. We developed custom tools for static and dynamic analysis of Swift binaries, which allowed us to perform a thorough investigation. Our analysis uncovered intriguing detection...
https://www.youtube.com/watch?v=1pJWqtBxb50
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Weaponizing Apple AI for Offensive Operations
Apple's on device AI frameworks CoreML, Vision, AVFoundation enable powerful automation and advanced media processing. However, these same capabilities introduce a stealthy attack surface that allows for payload execution, covert data exchange, and fully AI assisted command and control operations.
This talk introduces MLArc, a CoreML based C2 framework that abuses Apple AI processing pipeline for payload embedding, execution, and real time attacker controlled communication. By leveraging machine learning models, image processing APIs, and macOS native AI features, attackers can establish a fully functional AI assisted C2 without relying on traditional execution mechanisms or external dependencies.
Beyond MLArc as a standalone C2, this talk explores how Apple's AI frameworks can be weaponized...
https://www.youtube.com/watch?v=UooCY59nQSQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI-Powered Ransomware: How Threat Actors Weaponize AI Across the Attack Lifecycle
Are you prepared for the AI-powered ransomware attacks that are happening in the threat landscape right now? Threat actors aren't just deploying ransomware anymore, they're weaponizing artificial intelligence at every stage of their operations to maximize impact and evade detection. From AI-enhanced reconnaissance that profiles targets, to AI-generated ransomware, the ransomware playbook is changing. Joining us in January's livestream to discuss how AI is transforming the ransomware lifecycle is Foster Nethercott, a cybersecurity veteran and author of SANS' SEC535: Offensive AI: Attack Tools and Techniques course. We'll walk through each phase of modern ransomware operations - reconnaissance, initial access, lateral movement, data exfiltration, and impact, examining real-world examples of...
https://www.youtube.com/watch?v=g2fxSyoohZo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
No VPN Needed? Cryptographic Attacks Against the OPC UA Protocol
OPC UA is a standardized communication protocol that is widely used in the areas of industrial automation and IoT. It is used within and between OT networks, but also as a bridge between IT and OT environments or to connect field systems with the cloud. Traditionally, VPN tunnels are used to secure connections between OT trust zones (especially when they cross the internet), but this is often considered not to be necessary when using OPC UA because the protocol offers its own cryptographic authentication and transport security layer.
This makes OPC UA a valuable target for attackers, because if they could hijack a (potentially internet-exposed) OPC UA server they might be able to wreak havoc on whatever industrial systems are controlled by it. Therefore, I decided to take a look at the cryptography...
https://www.youtube.com/watch?v=OtTiz0Xvyw0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Lost in Translation: Exploiting Unicode Normalization
As web applications evolve, so do their data processing pipelines—handling Unicode normalization, encoding, and translation before storing or executing user input. But what if these same data transformations could be weaponized by attackers? This talk exposes how Unicode normalization flaws (such as visual confusables/best-fit mappings, truncation/overflows, case-mappings and entity decodings) lead to critical security bypasses—allowing attackers to evade WAFs, input filters, and backend logic to execute Remote Code Execution (RCE), Cross-Site Scripting (XSS), Server-Side Template Injection (SSTI), Open Redirects, and HTTP Response Splitting.
Using real-world attack data from Akamai's research team, this session will showcase live exploitation demos, explore the impact of vulnerabilities...
https://www.youtube.com/watch?v=ETB2w-f3pM4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Board of Directors 2026 Officer Elections
This meeting is to decide and vote upon which Directors will be the Officers of the OWASP Foundation, including votes for Chair, Vice Chair, Treasurer, and Secretary.
Minutes: https://board.owasp.org/meetings-historical/2026/202601-01.html
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=D57URHct0bE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Major Update to 13Cubed Courses: Chaos at Cobalt
Chaos at Cobalt, a major new practice scenario, is now available for Investigating Windows Endpoints, Investigating Windows Memory, and Investigating Linux Devices. Access the Additional Content module to get started!
🚀 Or enroll today at https://training.13cubed.com
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics #LinuxForensics
https://www.youtube.com/watch?v=CzF6DFhSfHw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - How to Become One of Them: Deep Cover Ops - Sean Jones, Kaloyan Ivanov
https://www.youtube.com/watch?v=aSOiPxOBs1E
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Inside the Shadows Tracking RaaS Groups, Cyber Threats - John Dilgen
https://www.youtube.com/watch?v=esKyHO5WjPU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Autonomous Video Hunter AI Agents for Real Time OSINT - Kevin Dela Rosa
https://www.youtube.com/watch?v=oHjQSpcP664
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - A Playbook for Integration Servers - Ryan Bonner, Guðmundur Karlsson
https://www.youtube.com/watch?v=wgf5GKrY3nc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Mapping the Shadow War From Estonia to Ukraine - Evgueni Erchov
https://www.youtube.com/watch?v=y-1_nKM8DRQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Building Local Knowledge Graphs for OSINT - Donald Pellegrino
https://www.youtube.com/watch?v=yIUfntW_TxY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - OSINT & Modern Recon Uncover Global VPN Infrastructure - Vladimir Tokarev
https://www.youtube.com/watch?v=4HGFlZZfWc8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Pretty Good Pivot - Simwindie
https://www.youtube.com/watch?v=6mykx1zS1yo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - enumeraite: AI Assisted Web Attack Surface Enumeration - Özgün Kültekin
https://www.youtube.com/watch?v=IzsBS_E2RVY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - OSINT Signals Pop Quiz - Master Chen
https://www.youtube.com/watch?v=L-ZqeZbiWn8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Investigating Foreign Tech from Online Retailers - Michael Portera
https://www.youtube.com/watch?v=MAtllbHmxP4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DEF CON 33 Recon Village - Attack Surface in Motion - Muslim Koser
https://www.youtube.com/watch?v=N7w6FklAmVA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
My Favorite Bug Bounty Findings In 2025
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
Try Snyk's Cursor Integration 👉🏼 https://snyk.co/nahamsec-integration
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023...
https://www.youtube.com/watch?v=zvUglkPWals
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Rise of the Bionic Hacker: Real Data Shaping Cybersecurity in 2026
AI is reshaping the cybersecurity landscape, but human creativity is still uncovering what machines miss.
The 2025 Hacker-Powered Security Report, The Rise of the Bionic Hacker, reveals how attacker economics, shifting vulnerability trends, and AI disruption are reshaping security programs worldwide. Watch HackerOne, PortSwigger, IAC, and leading security researchers discuss where peers are investing, what hackers see in the wild, and how to turn data into decisive action for your security program.
Featuring:
James Kettle — Director of Research, PortSwigger
Justin Gardner — Host, Critical Thinking podcast & Bug Bounty Hunter
Luke (Hakluke) Stephens — Founder & CEO, Haksec
Mehan Kasinath — VP Enterprise Information Security, IAC
Jewel Timpe — Director of Triage, HackerOne
Read...
https://www.youtube.com/watch?v=MSrcyJaMeA4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Inside H1-6102: Live Hacking Event with Salesforce in Sydney
At H1-6102 in Sydney, security researchers from across the globe came together with Salesforce to proactively stress-test defenses and share their expertise. From deep technical findings to collaborative problem-solving, this event shows how the research community continues to strengthen security one report at a time.
Watch the highlights and meet the people behind the discoveries.
For more information about HackerOne, visit https://www.hackerone.com/
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
◇ Instagram → https://www.instagram.com/hacker0x01/
https://www.youtube.com/watch?v=K0bbHCJoWWU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global Board of Directors - December 2025
Minutes here: https://board.owasp.org/meetings-historical/2025/202512.html
Finance summary here: https://youtu.be/ZBjQmebdLsA
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=dKrH3xTstO8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Manipulating Memory with Cheat Engine - Hacky Christmas [NahamCon 2025 CTF]
🎅 Video walkthrough for the Hacky Christmas challenge I made for the NahamCon Capture the Flag (CTF) competition 2025 Winter Edition (organised by @NahamSec) It was a game hacking challenge (Unity) where players were expected to escape the ice box (teleport) and then obtain more than 1 million points. The easiest way to do this is to identify those values (coordinates and points) in memory, and modify them! Write-ups/tutorials aimed at beginners - Hope you enjoy 🙂 #NahamCon #NahamCon2025 #NahamConCTF #CTF #GameHacking #CheatEngine
Full write-ups for all my NahamCon 2025 challenges: https://cryptocat.me/blog/ctf/2025#nahamcon-winter
Want to learn more about hacking games with cheat engine? Check out my full tutorial series over on the @intigriti channel: https://www.youtube.com/watch?v=ku6AtIY-Lu0&list=PLmqenIp2RQcg0x2mDAyL2MC23DAGcCR9b...
https://www.youtube.com/watch?v=fs9WeNkUB4M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Extracting the unseen: Real-world RAM acquisition and analysis from Android devices
Extracting the unseen: Real-world RAM acquisition and analysis from Android devices
Alex Coley, Digital Forensic Specialist - MSAB
DFIR Prague 2025
Volatile memory on Android devices often contains critical evidence — Encryption keys, credentials, and transient user data that traditional extractions miss. This session demonstrates real-world RAM acquisition and analysis, showing how to safely recover, interpret, and correlate volatile artifacts with static data. This session will offer you a clear view of practical workflows, essential tools, and actionable tips to enhance mobile forensic investigations
https://www.youtube.com/watch?v=p0CpWxfQAjI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Keynote by Adam Shostack: Stop Trying to "Manage Risk"
They say that risk management is fundamental to cybersecurity. Whoever they are, they're wrong, and it's hurting us. We spend inordinate amounts of energy on risk analysis, but that's simply not how executives are making decisions. This talk will cover specific examples of risk requirements, why those requirements are impossible to satisfy, and what we might do to address that tension.
Adam Shostack
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=THSfJIlPGPk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Top 10 Annoucement
Presentation sides: https://static.sched.com/hosted_files/owaspglobalappsecusa2025/35/DC2025%20-%20OWASP%20Top%20Ten%202025.pptx
The OWASP Top 10:2025 provides an updated view of modern applications' most common and impactful security risks. Based on both industry data and community survey input, the Top 10 is designed as an awareness tool, helping teams baseline the most relevant security concerns. This talk will walk through the changes since the 2021 edition, highlighting where categories have shifted, merged, or expanded to reflect the changes over the last four years. Each risk category will be introduced at a high level, covering its main issues and offering context for how organizations can use the list as a reference point in their security programs.
Tanya Janca
Victoria, Canada
https://twitter.com/shehackspurple
https://www.linkedin.com/in/tanya-janca
Tanya...
https://www.youtube.com/watch?v=yGOXewm3DsA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Keynote by Daniel Miessler: The Future of AppSec Is Continuous Context
My name is Daniel Miessler (https://danielmiessler.com/about/) and I'm a Cybersecurity / AI engineer and founder based out of the San Francisco Bay Area who's been writing online since 1999 (https://danielmiessler.com/archives/)
My goal is to help build a positive, human-based AI future, which I call Human 3.0 (https://danielmiessler.com/blog/how-my-projects-fit-together/)
In order to do that, I am building AI products that upgrade people and organizations—rather than try to replace them.
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=C4L5hPYl1Os
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Digital forensics and security: Automate audits, investigations and response with AWX and Ansible
Enterprise digital forensics and security with open tools: Automate audits, computer forensics investigations and incident response with AWX and Ansible
Alessandro Fiorenzi, Cyber Security & Digital Forensics Expert - SF Security & Forensics
DFIR Europe Prague
In modern enterprises, managing digital forensics, incident response, and security audits across hundreds of endpoints and cloud systems is challenging. This session demonstrates how open-source automation tools — AWX and Ansible — can streamline forensic investigations, compliance audits, and incident response. Attendees will learn how agentless automation can collect evidence scientifically and at scale, ensuring consistency, traceability, and efficiency across heterogeneous environments without expensive commercial solutions....
https://www.youtube.com/watch?v=AG4HPlgotco
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tool: Forensic WACE - A multi-threaded tool for forensic analysis of What's App chats
Tool: Forensic WACE - A multi-threaded tool for semantic forensic analysis of What's App chats using AI tools
Daniele Monte, Senior Software Engineer – University of Bari
Alessio Palmieri, Consultant – University of Bari
DFIR Prague 2025
Forensic WACE is a free, multi-threaded tool designed for semantic forensic analysis of WhatsApp databases on iOS and Android. Its web-based interface enables multiple investigators to work concurrently on analyses and report generation, while ensuring data remains secure and isolated. In this session, you'll learn how Forensic WACE leverages AI to perform in-depth forensic analysis, with all results centralized in an intuitive web interface to support efficient, collaborative, and reproducible investigations.
https://www.youtube.com/watch?v=1ozfZ0CEZbo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
When the threat group doesn't leave: Incident response under fire
When the threat group doesn't leave: Incident response under
Eran Liloof, Head of Threat Detection – Vega Security
DFIR Prague 2025
What happens when you face one of the most aggressive, capable, and determined threat group - while they're still active in the network? This session presents a real-world cyber extortion case where investigators battled a live adversary within a complex environment. Attendees will explore the threat group's TTPs, a detailed attack timeline, critical containment and forensic challenges, and key incident management dilemmas. Beyond a war story, this deep-dive provides actionable lessons for IR professionals, threat hunters, SOC analysts, and incident managers, offering guidance on avoiding costly mistakes when responding to live, ongoing attacks.
#cybercrime...
https://www.youtube.com/watch?v=p3SEEdV425I
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Mobile device hardening: A forensic comparison of advanced protection programmes in IOS and Android
Mobile device hardening: A forensic comparison of advanced protection programmes in IOS and Android
Luca Cadonici, Head of Masters Programme in Cybersecurity – European Forensic Institute
DFIR Prague 2025
How do Apple's Lockdown Mode and Advanced Data Protection compare to Google's Advanced Protection introduced in Android 16? Designed to protect high-risk users from sophisticated threats, these programs enforce device and cloud-level security. Join us to explore architectural differences between iOS and Android, understand how these protections affect digital forensic workflows, and gain practical guidance for identifying, preserving, and analysing data on hardened devices. Come away with practical insights on how to adapt your investigative techniques for today's increasingly...
https://www.youtube.com/watch?v=a-_di0nfOL8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tool: Location log analysis of Google Maps IOS
Tool: Location log analysis of Google Maps IOS
Ludovico Nigro, Graduate Cybersecurity Graduate – University of Bari
Antonio Roberto Consalvi, Software Engineer – Studio D'Ingegneria Consalvi
DFIR Prague 2025
In 2024, Google shifted Google Maps location history storage from the cloud to mobile devices, introducing the location-history.json file on iOS. This presentation provides an in-depth forensic analysis of this new format, exploring semantic segments such as “visit,” “activity,” and “timelinePath,” along with their temporal structure and investigative value. We will examine the challenges posed by the removal of raw signals, including continuous coordinates, error margins, and data sources. Additionally, a multi-platform open-source tool developed for parsing, interactive...
https://www.youtube.com/watch?v=8GE-fIw7sb8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
PDF forensics and authenticity detection
PDF forensics and authenticity detection
Jean-Philippe Noat, Senior Solution Expert – Celebrite
DFIR Prague 2025
This presentation delves into the field of PDF forensic analysis and unveils practical techniques to identify non-original (tampered, altered, or fabricated) PDF documents. Participants will learn how investigators use digital clues and metadata to distinguish genuine PDFs from forged ones, equipping them with skills essential for fraud detection, compliance audits, and legal document verification using open-source tools.
#cybercrime | #dfir
https://www.youtube.com/watch?v=ELcsKcR_seo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
MacOS telemetry vs EDR telemetry - Which is better?
MacOS telemetry vs EDR telemetry - Which is better?
Fouad Animashaun, Security Engineer – Dropbox
DFIR Prague 2025
As macOS adoption grows in enterprise environments, threat actors are increasingly targeting these systems, leaving incident responders to adapt their investigative approaches. While Endpoint Detection and Response (EDR) solutions provide broad visibility, Apple's Unified Logging System (AUL) often captures deeper, host-level telemetry that EDR tools miss. This session will compare EDR telemetry with macOS unified logs, demonstrating scenarios where unified logs answer key forensic questions that EDR cannot. Understand how to leverage AUL in investigations, use Private Data Logging, and work within log retention limitations. You will leave with actionable methods to enhance...
https://www.youtube.com/watch?v=V6VnQ-h4K-o
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tool: The only ‘Kanvas' you need when spreadsheets fail your IR case management
Tool: The only ‘Kanvas' you need when spreadsheets fail your IR case management
Jinto Antony, Senior Investigator, Incident Response - With secure
DFIR Prague 2025
Incident responders often rely on the “Spreadsheet of Doom” (SOD) to track findings and observations, but managing, updating, and ext open-source case extracting insights from these spreadsheets can be cumbersome. Kanvas is a management tool designed to replace the SOD with a streamlined, Python/Qt-based desktop interface. What are Kanvas' new features? How does it reduce manual effort in both investigation and documentation? Learn how Kanvas simplifies IR case management without requiring heavy infrastructure, thus providing a practical, community-driven alternative to existing tools.
#cybercrime | #dfir
https://www.youtube.com/watch?v=zdQf9GmcnbQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Home automation and IoT as a source of evidence: Forensic analysis of Home Assistant
Home automation and IoT as a source of evidence: Forensic analysis of Home Assistant
Andrea Lazzarotto, Digital Forensics Consultant - Andrea Lazzarotto
DFIR Prague 2025
As smart homes become more widespread, they present a growing but often overlooked source of digital evidence. This session explores forensic opportunities within Home Assistant, one of the most popular home automation platforms. By analysing its data, investigators can uncover user movements, device usage, and environmental conditions—correlated with precise timestamps. Such insights can corroborate or challenge statements, offering powerful evidential value in modern investigations.
#iot | #cybercrime | #dfir
https://www.youtube.com/watch?v=G0WjLYjx_rw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
This Feature in Burp Suite Low-Key Changes Everything
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=cy-crkgLPvI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hunting payloads in Linux extended file attributes
Hunting payloads in Linux extended file attributes
Xavier Mertens, Freelance Cybersecurity Consultant - Xameco SRL
DFIR Prague 2025
Linux Extended File Attributes provide functionality similar to NTFS Alternate Data Streams (ADS). While often used for legitimate purposes, they can also be abused to conceal malicious content. Attackers may hide payloads, encrypted data, or other artifacts within these attributes —making detection and forensic analysis more challenging. This session will demonstrate both sides of the equation: How adversaries can hide a simple payload in extended attributes and how defenders can detect and investigate such misuse. Gain practical insights into the offensive and defensive techniques surrounding Linux extended attributes, to help you strengthen your hunting...
https://www.youtube.com/watch?v=etnhELMsSOI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The art of concealment: How cybercriminals are becoming and remaining anonymous
The art of concealment: How cybercriminals are becoming and remaining anonymous
Mick Deben, Cybersecurity Consultant - DMC Group B.V.
DFIR Prague 2025
The attribution of cybercrime remains one of the greatest challenges for investigators, largely due to the extensive concealment measures employed by threat actors. While much research focuses on tactics, techniques, and procedures (TTPs) used in the execution of cyberattacks, little attention has been given to the methods criminals use to hide their identities and activities. This session introduces CLOAK (Concealment Layers for Online Anonymity and Knowledge). Developed through the qualitative analysis of countless operational security guides from the clear and dark web, CLOAK catalogues more than 1,300 unique concealment TTPs spanning...
https://www.youtube.com/watch?v=xUqUY493bM4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
HackerOne on AI-Driven Security: Community, Risk, and Innovation
At HackerOne, we believe that the future of security involves a security researcher community working together with customers by combining the use of powerful AI and automation.
In this video, HackerOne leaders, customers, and security researchers share how AI, automation, and the global researcher community work together to give defenders a competitive edge. From accelerating code reviews to predicting future vulnerabilities, the next era of security will be defined by collaboration between human expertise and powerful AI systems.
To learn how HackerOne is redefining AI security, visit https://www.hackerone.com/solutions/ai
▼ Keep up with us ▼
◇ LinkedIn → https://www.linkedin.com/company/HackerOne
◇ Twitter → https://twitter.com/Hacker0x01
◇ Instagram → https://www.instagram.com/hacker0x01/...
https://www.youtube.com/watch?v=6qbz-oB_ESI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global Board of Directors - November 2025
Minutes here: https://board.owasp.org/meetings-historical/2025/202511.html
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=BSGa5g8OlRs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Adversarial Image Attacks Explained
Adversarial images are specially crafted visuals that embed hidden prompts or instructions, invisible to humans but detectable by AI systems, allowing attackers to manipulate AI behavior through prompt injection.
These attacks exploit image processing pipelines like OCR and scaling, potentially leading to data leaks, unauthorized actions, or command execution in tools like Google Gemini and Vertex AI.
To defend against them, treat all images as untrusted inputs, disable unnecessary automated processing, and use advanced tools like PromptShield™ to scan and block risky content in real time.
Read the full article: https://purplesec.us/learn/adversarial-image-attacks/
🔒 Secure Your LLMs With PromptShield™
---------------------------------------------------------------
Sitting between...
https://www.youtube.com/watch?v=fNhXqDOoMfA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Stay Ahead of Ransomware - Threat Hunting for Ransomware and Cyber Extortion
Are YOU hunting for ransomware actors who may be operating in your environment RIGHT NOW?! If you aren't taking a proactive approach to hunting for ransomware and cyber extortion operations, you may find yourself in quite the predicament. Many times, organizations learn about a ransomware attack far too late – be it identification of ransom notes on a variety of hosts, a system that is no longer functioning as expected, notification from a 3rd-party, or other. Joining us this month to talk about threat hunting as related to ransomware activity is Sydney Marone, one of the best threat hunters on the planet! Sydney is the co-founder of the THOR Collective, co-author of the PEAK Threat Hunting Framework, experienced speaker, and much more. Bring your questions and come join the conversation...
https://www.youtube.com/watch?v=ZQAwTrdukI0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Mother Printers: Full Exploit Chain Analysis + Demo [HackingHub]
Mother Printers is a multi-stage challenge (web/rev/pwn) I created for @HackingHub_io. It was inspired by the Brother Printers CVEs discovered by Stephen Fewer (@OfficialRapid7) and extended by Star Labs (@STAR-Labs) for Pwn2Own 2025. Players must first enumerate a printer manufacturer website. When downloading the firmware, they will spot an open directory listing with a "printer_build" binary and a remote printer configuration (exposed secrets). While reversing the binaries, they find a similar chain of vulnerabilities to the original research; info leak, authentication bypass (default password generation), buffer overflow in the referer header (3-byte overwrite) and an SSRF. The challenge is designed so that players must chain all vulnerabilities together, i.e. a vulnerability can only...
https://www.youtube.com/watch?v=ebNYtX_8lOY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
I Got A Remote Code Execution On A Wordpress Site Using AI
Check out Neo here 👉🏼 https://neo.projectdiscovery.io
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to...
https://www.youtube.com/watch?v=AnVONITvWw4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
13Cubed AMA - Answering Your Questions!
In this special 13Cubed episode, I answer questions collected from the community!
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
#Forensics #DigitalForensics #DFIR #ComputerForensics
https://www.youtube.com/watch?v=duz5BoZUly8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Avoid getting hacked during the holidays with these 3 critical tips!
The holidays bring joy, celebration and unfortunately, hackers who never take time off. This video explores three major cybersecurity risks during the holiday season and how to protect yourself and your family. From toy drop scams targeting eager parents to smartwatch security vulnerabilities and home Wi-Fi risks during gatherings, we cover practical steps you can take to keep your celebrations scam-free. Learn how to spot fake vendor sites, secure your wearable devices, and protect your guests when they connect to your home network.
0:00 - Intro: Hackers don't take holidays off
0:20 - Holiday toy scams and livestream drops
1:15 - How to avoid toy purchasing scams
1:45 - Smartwatch security risks
2:35 - Protecting your smartwatch from hackers
3:05 - Securing your home Wi-Fi for holiday gatherings
4:00...
https://www.youtube.com/watch?v=6PIXFY-7D8k
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Free Post Recon Course and Methodology For Bug Bounty Hunters
Signup for Hostinger and get 10% off using code NAHAMSEC 👉🏼 https://hostinger.com/nahamsec
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023...
https://www.youtube.com/watch?v=RYdTp4a9S34
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global Board of Directors - October 2025
A slightly delayed October Board meeting to match up with Global AppSec USA
Minutes here: TBA
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=vxiMBv9VOfM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How to Use Nuclei And Automate Cross-Site Scripting Vulnerabilities
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
Start Hacking with my Nuclei Masterclass for half off👉🏼 https://hhub.io/NucleiYT
Buy all of my bug bounty courses for the price of one👉🏼https://hhub.io/blackfriday2025
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿...
https://www.youtube.com/watch?v=WCXW9uKYm48
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
This Is How Max Verstappen Was Hacked
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=zL-rFdGJYzQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Robot is Watching You [Not Sci-Fi Anymore]
The robot is watching you, @aliasrobotics7887 discovered.
And it's sending all data to remote servers.
Alias then put an AI Hacking Agent (CAI) inside the robot.
CAI hacked the robot and the cloud infrastructure from within.
Read their entire 100-page paper, reporting what they did: https://arxiv.org/pdf/2509.14096
https://www.youtube.com/watch?v=0v1M63zwt7Y
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
This Hacker Made Over ,000 Hacking AI
Signup for the GraySwan Academy 👉🏼 https://app.grayswan.ai/arena
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023...
https://www.youtube.com/watch?v=xy1vQOHGQQY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
IDA Free Reverse Engineering - Step-by-Step EXE Analysis
Step-by-step reverse engineering tutorial with IDA Free covering decompiling, types, enums, function definitions, and naming for EXEs.
Sample can be found on unpac.me
7b5b060d9013725413f3f77719d0881035246b281e18005c0040e78a32e1c6cc
Full tutorial series on the OALABS Patreon
https://www.patreon.com/collection/1259251?view=expanded
https://www.youtube.com/watch?v=u1ZEh3bb6h4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hidden Product Activation and Serial Keygen - "Ultimate Calculator 3000" [Rev/Web Challenge]
🚩 Video walkthrough for the "Ultimate Calculator 3000" (rev/web) challenge I created and hosted on my website (https://cryptocat.me) 😺 Players had to locate a hidden validator routine inside the calculator binary, uncover a secondary HTTP service, and obtain the support team's offline validation tool. Reversing the Go binary exposed an HMAC-based serial check, allowing crafted serials to pass verification and reveal the flag 😎 #CTF #Challenge #CryptoCat
Check out the accompanying writeup here: https://cryptocat.me/blog/ctf/monthly/cryptocat/1025/ultimate_calculator/
Join discord for source code and early access to future challenges: https://discord.cryptocat.me
🐛CryptoCat CTF Challenges🐞
https://challenge.cryptocat.me - https://discord.gg/qHbAN3wfRK
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00...
https://www.youtube.com/watch?v=lRJno96za5A
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
No Code Bug Bounty Automation Using n8n
Sign up for Hostinger's Black Friday Sale 👉 https://hostinger.com/nahamsec gland get 10% off using the code nahamsec
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in...
https://www.youtube.com/watch?v=PemrRgzckVE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Easy Way to Analyze Linux Memory
In this episode, we'll take a look at a quick and easy way to find the Intermediate Symbol File (ISF) for the Linux memory image you're analyzing. This method will save you time and help streamline your memory analysis workflow.
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
00:37 - Demo
🛠 Resources
Abyss-W4tcher ISFs:
https://github.com/Abyss-W4tcher/volatility3-symbols
leludo84 ISFs:
https://github.com/leludo84/vol3-linux-profiles
Volatility-ready URLs:
https://raw.githubusercontent.com/Abyss-W4tcher/volatility3-symbols/refs/heads/master/banners/banners.json
https://raw.githubusercontent.com/leludo84/vol3-linux-profiles/refs/heads/main/banners-isf.json
#Forensics #DigitalForensics #DFIR #ComputerForensics...
https://www.youtube.com/watch?v=W40gdWNdwUI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Best Hacking Tools For 2026
LIKE and SUBSCRIBE with NOTIFICATIONS ON if you enjoyed the video! 👍
📚 If you want to learn bug bounty hunting from me: https://bugbounty.nahamsec.training
💻 If you want to practice some of my free labs and challenges: https://app.hackinghub.io
💵 FREE 0 DigitalOcean Credit:
https://m.do.co/c/3236319b9d0b
🔗 LINKS:
📖 MY FAVORITE BOOKS:
Bug Bounty Bootcamp: The Guide to Finding and Reporting Web Vulnerabilities -https://amzn.to/3Re8Pa2
Hacking APIs: Breaking Web Application Programming Interfaces - https://amzn.to/45g4bOr
Black Hat GraphQL: Attacking Next Generation APIs - https://amzn.to/455F9l3
🍿 WATCH NEXT:
If I Started Bug Bounty Hunting in 2024, I'd Do this - https://youtu.be/z6O6McIDYhU
2023 How to Bug Bounty - https://youtu.be/FDeuOhE5MhU
Bug Bounty Hunting...
https://www.youtube.com/watch?v=l5zrNrNEJoA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The AI Black Box Problem - [Latent Space Exploration]
Latent space exploration. Created from multiple sources using NotebookLM.
https://www.youtube.com/watch?v=HfCUbauGUNs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI Ethics That Work: Privacy, Fairness & Security
How do we build AI security that is ethical, resilient, and trustworthy without turning “ethics” into a checkbox?
Host Jason Firch sits down with Tom Vazdar (Chief AI Officer, PurpleSec) and Josh Salvage (CTO, PurpleSec) to unpack the real-world tensions between privacy, fairness, explainability, regulation, human oversight, and adversarial threats.
If you're a security leader, engineer, or business decision-maker, this conversation will help you separate PR from practice and design AI systems that respect rights, dignity, and safety—while staying practical for SMBs and enterprises alike.
🔒 Secure Your LLMs With PromptShield™
---------------------------------------------------------------
Sitting between users and your AI models, PromptShield™ detects, blocks, and educates...
https://www.youtube.com/watch?v=lsZ0h4_b5T0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global Board of Directors - September 2025
Minutes here:
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=voziHgnXMps
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
AI Security Frameworks: Must-Know Challenges & Solutions For 2025
Uncover the biggest challenges organizations face in implementing AI security frameworks and explore expert solutions to stay ahead in 2025!
Join Security Beyond The Checkbox host Jason Firch, alongside PurpleSec's Chief AI Officer Tom Vazdar, and CTO Joshua Selvidge, as they break down the essentials of securing AI systems. From cloud-based deployments to zero trust models, learn how to protect critical infrastructure like hospitals and banks from emerging threats like data poisoning and model manipulation.
Discover why frameworks like ISO 42001 and NIST AI RMF are vital for governance, ethics, and robust security. Gain insights into the importance of industry-academia-policy collaboration to strengthen AI security standards.
🔒 Secure Your LLMs With PromptShield™
---------------------------------------------------------------
Sitting...
https://www.youtube.com/watch?v=UJ7FFF33kik
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Shadow AI: The Silent Cybersecurity Threat Businesses Can't Ignore
In this episode of Security Beyond the Checkbox, host Jason Firch sits down with PurpleSec's Chief AI Officer Tom Vazdar, and CTO Joshua Selvidge to unpack Shadow AI, which is the unauthorized use of AI tools like ChatGPT that mirrors the risks of Shadow IT.
As SMBs grapple with emerging threats like ransomware and phishing, Shadow AI is exploding due to its easy access and massive productivity gains, but it brings serious dangers if left unchecked. We dive into why employees turn to these tools (often non-maliciously) to boost efficiency, and the real risks: data leaks, intellectual property theft, regulatory violations under GDPR or HIPAA, and reputational harm.
Hear real-world examples, including Samsung's ban on ChatGPT after engineers leaked proprietary code, and Air Canada's chatbot...
https://www.youtube.com/watch?v=MLUBbgReax8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Brother Printers Vulnerabilities Explained - Info Leak, Auth Bypass, Buffer Overflow, SSRF, DoS
🖨 Print Scan Hacks: Multiple vulnerabilities were identified across various Brother devices by Stephen Fewer (@OfficialRapid7) 🔬 In this video, we'll analyse the zero-day research whitepaper and review the 8 vulnerabilities/exploits (CVE-2024-51977 through CVE-2024-51984) that were disclosed. Topics covered include info leak, remote auth bypass, buffer overflow, SSRF, DoS and credential exposure. Write-ups/tutorials aimed at beginners - Hope you enjoy 🙂 #Vulnerability #Research #OffSec
🐛Brother Printer Vulnerability Research🐞
Blog: https://www.rapid7.com/blog/post/multiple-brother-devices-multiple-vulnerabilities-fixed
Whitepaper: https://assets.contentstack.io/v3/assets/blte4f029e766e6b253/blt6495b3c6adf2867f/685aa980a26c5e2b1026969c/vulnerability-disclosure-whitepaper.pdf
Exploits:...
https://www.youtube.com/watch?v=--SaQKmcyiU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
IDA Free Reverse Engineering - Step-by-Step DLL Analysis
Step-by-step reverse engineering tutorial with IDA Free covering decompiling, types, enums, function definitions, and naming for DLLs.
Sample can be found on unpac.me
93f9703cc7339014cd1bc82da0ab8909957112b93fba2430b5ee90a1d424a5ed
Full tutorial series on the OALABS Patreon
https://www.patreon.com/collection/1259251?view=expanded
https://www.youtube.com/watch?v=tbIjHJ1ygBY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Secure Code Inspired Offensive Payloads [For Pentesters]
A compilation of attack vectors and payloads for penetration testing and offensive security, inspired from the OWASP Secure Code Review Guide.
I've guided NotebookLM to create this presentation for offensive pentesters.
https://www.youtube.com/watch?v=XqwJusDJXEQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Will AI Replace Digital Forensics Experts?
Is AI going to replace digital forensic investigators? In this episode, we'll test a local instance of DeepSeek-R1 in Windows forensics to see how it compares to a human investigator. Let's find out if AI can handle the job!
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
01:23 - The Questions Begin
10:43 - Closing Thoughts
🛠 Resources
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics #AI #DeepSeek
https://www.youtube.com/watch?v=lvkBtIhvThk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global Board of Directors Meeting - August 2025
Minutes here: https://board.owasp.org/meetings-historical/2025/202508.html
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=3qxGpzgR84A
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Cornucopia Abuse Case Modeling
Visit https://cornucopia.owasp.org for all things OWASP Cornucopia!
Learn how to play, download FREE resources, explore cards in detail, and access the repo
Play online https://copi.securedelivery.io/
Managed by the OWASP® Foundation
https://owasp.org/
https://www.youtube.com/watch?v=vLYzId7-ijI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC33 - Red Team Village - Recap
Thank you to everyone who attended the village this year at DEF CON! Another huge thank you to our core team, sponsors, volunteers, goons, and DEF CON!
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=oP27VgfmfuY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
HTTP Pipelining or Request Smuggling? - No More False Positives
Based on the amazing work of James Kettle from Portswigger. You can find it here: https://portswigger.net/research/how-to-distinguish-http-pipelining-from-request-smuggling.
I've guided NotebookLM to create this presentation for offensive pentesters.
https://www.youtube.com/watch?v=SNQlR6jiGeg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Leaking Passwords via CSS Injection - "Fancy Login Form" [WHY CTF 2025]
🚩 Video walkthrough for the "Fancy Login Form" web challenge featured in the 2025 WHY CTF competition. The challenge involved exploiting a URL-based redirection to take control of a CSS file, then using blind exfiltration to extract each character of the admin's password from the login form field 😎 #CTF #Challenge #WHY2025
Check out the accompanying writeups here: https://cryptocat.me/blog/ctf/2025/#why/
Join my discord server if you have any questions: https://discord.cryptocat.me
🐛What Hackers Yearn (@WHY2025NL) CTF🐞
https://ctf.why2025.org
https://why2025.org
https://discord.gg/fkn7qW3GRT
https://ctftime.org/event/2680
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00 Intro
0:46 Fancy Login Form
2:27 Hijacking CSS file
6:10 Blind data exfiltration
9:37...
https://www.youtube.com/watch?v=jUjlj2z5jJk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Analysing the DOM to find Reflected XSS
Stuck watching YouTube videos about bug bounty hunting rather than a bounty hitting your inbox? In this series I partner with Bugcrowd to bring you everything you need to know to find their most common first bugs. In this video we explore one of the common first vulnerabilities - Reflected Cross-Site Scripting (XSS). Learn the basics of XSS, how to identify and exploit this vulnerability, and see a practical demonstration you can replicate on your own targets. With step-by-step methodology and tips, this episode will guide you through finding and validating the internets most common first bug.
This series couldn't happen without the support of our sponsor Bugcrowd, Bugcrowd is the best place to start hacking with a wide range of public and private programs from APIs to Desktop Applications...
https://www.youtube.com/watch?v=CpV3XDqzYyE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
HTTP/1.1 - The Desync Endgame
Based on the amazing work of James Kettle of @PortSwiggerTV found at https://portswigger.net/research/http1-must-die.
I've guided NotebookLM by @Google to create this presentation for offensive pentesters.
https://www.youtube.com/watch?v=zs1rZnZuJ6A
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
On HTTP Request Smuggling - RFC 9110 Style
Based on the RFC 9110, I've guided NotebookLM by @Google to create this presentation for offensive pentesters, specifically on HTTP Methods.
RFC 9110: https://www.rfc-editor.org/rfc/rfc9110.html
https://www.youtube.com/watch?v=CvEBA_Sm-mw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OWASP Global AppSec EU 2025 Closing Ceremony
Watch the closing ceremony to the OWASP Global AppSec EU 2025 conference.
https://www.youtube.com/watch?v=Fe_C8qGFTvI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
HTTP Methods for Offensive Pentesting
Based on the RFC 9110, I've guided NotebookLM by @Google to create this presentation for offensive pentesters, specifically on HTTP Methods.
RFC 9110: https://www.rfc-editor.org/rfc/rfc9110.html
https://www.youtube.com/watch?v=ZtoPYQD0rXs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC33 - Red Team Village x Amazon
Thank you for being one of our platinum sponsors!
Additional information about Amazon can be obtained from https://www.aboutamazon.com/
They're Hiring!: https://amazon.jobs/content/en/teams/amazon-security/devices-services
Twitter/X: https://x.com/amazon
LinkedIn: https://www.linkedin.com/company/amazon/
_________________________________________________________________________
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter/X: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=-KIEqwVejSE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Behind the Book: Threat Hunting macOS with Jaron Bradley
In this episode, I sit down with Jaron Bradley, author of the upcoming book Threat Hunting macOS. With the recent release of the new 13Cubed training course Investigating macOS Endpoints, this felt like the perfect time to bring Jaron on the channel to discuss his new book — a resource I believe will be an excellent companion to the course.
📘 Order Jaron's Book – Threat Hunting macOS
https://themittenmac.com/threat-hunting-book/
🌐 Visit Jaron's Website – The Mitten Mac
https://themittenmac.com/
🎓 Learn macOS Forensics!
https://training.13cubed.com/investigating-macos-endpoints
#Forensics #DigitalForensics #DFIR #ComputerForensics #macOSForensics
https://www.youtube.com/watch?v=8Uj2NbWnU6M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC33 - Red Team Village x Flare
Thank you for being one of our platinum sponsors!
Additional information about Flare can be obtained from https://flare.io/.
Twitter/X: https://twitter.com/FlareSystems
LinkedIn: https://www.linkedin.com/company/flare-systems-inc
Discord: https://discord.gg/qRGBT2TcEV
YouTube: https://www.youtube.com/channel/UCU5Nr_7GpdxgxPOhuWuvXVg
_________________________________________________________________________
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter/X: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=xapuRA5uEbg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Still not found your first bug? Try IDORs
Stuck watching YouTube videos about bug bounty hunting rather than your inbox? In this series I partner with Bugcrowd to bring you everything you need to know to find their most common first bugs. In this episode we're talking about the ever popular IDOR, and while yes, I am aware I have made videos on this topic many times, it's still a solid choice for your first bug, difficult to automate and scale, yet easy to understand and test for. Its tediousness means that top hackers often skip them in favour of trickier bugs, making it perfect for newer bug bounty hunters to focus on.
This series couldn't happen without the support of our sponsor Bugcrowd, Bugcrowd is the best place to start hacking with a wide range of public and private programs from APIs to Desktop Applications and everything...
https://www.youtube.com/watch?v=8Uva1su3goc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC33 - Red Team Village x White Knight Labs
Thank you for being one of our platinum sponsors!
Additional information about White Knight Labs can be obtained from https://whiteknightlabs.com.
Twitter/X: https://twitter.com/WKL_cyber
LinkedIn: https://www.linkedin.com/company/white-knight-labs/
Discord: https://discord.gg/qRGBT2TcEV
_________________________________________________________________________
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter/X: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=RULalD2__Lg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC33 - Red Team Village x Kindo
Thank you for being one of our platinum sponsors!
Additional information about Kindo can be obtained from https://www.kindo.ai/.
Twitter/X: https://x.com/kindoai
LinkedIn: https://linkedin.com/company/kindo-ai
YouTube: https://www.youtube.com/channel/UC9ahwU5unSzp0ytNPcjVg8g
_________________________________________________________________________
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter/X: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=PT7zVhbdvpk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Windows Memory Forensics Challenge
Welcome to a special Windows Memory Forensics Challenge from 13Cubed. This is an excellent opportunity to get some hands-on practice with Windows memory forensics. You'll find the questions below, as well as a link to download the memory sample needed to answer those questions.
🎉 Check out the official training courses from 13Cubed at https://training.13cubed.com!
🛑 CONTEST IS CLOSED 🛑
All winners have been selected. We still encourage you to participate in the lab, as we believe it will serve as an excellent practice opportunity. If you do participate, please consider creating a video or blog-based walkthrough of the process, as it would be a valuable resource for the community!
⚠️ CAUTION ⚠️
This memory sample contains a simulated ransomware for educational purposes....
https://www.youtube.com/watch?v=6JN6iAenEoA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Top Skills Cybersecurity Professionals Need In 2025
Cybersecurity professionals must blend core technical skills with AI expertise to stay relevant as the field evolves. The following skills are essential for building a practical, effective defense in an AI-driven world.
📖 Read the full article: https://purplesec.us/learn/ai-replacing-cybersecurity-jobs/
Tom Vazdar is the Chief AI Officer at PurpleSec and brings more than two decades of cybersecurity expertise to this discussion. He is an expert in AI and leads the development of advanced cybersecurity strategies, enhancing data protection and compliance. As an AI strategist and mentor, Tom advocates for ethical AI integration.
About The Experts
------------------------------
Jason Firch, MBA
https://purplesec.us/about-us/leadership/jason-firch/
Tom Vazdar
https://purplesec.us/about-us/leadership/tom-vazdar/
AI...
https://www.youtube.com/watch?v=KbyAwGCXfCc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
New Course! Investigating macOS Endpoints
Check out Investigating macOS Endpoints, a comprehensive macOS forensics training course from 13Cubed! Starting with fundamental principles, Investigating macOS Endpoints advances to encompass log analysis, file systems, forensic artifacts, persistence mechanisms, evidence collection, and more! This course offers extensive hands-on practice and a capstone involving the analysis of a compromised system. Tailored for both beginners and seasoned professionals, it serves as an ideal resource for mastering macOS forensics!
🎉 Enroll today at https://training.13cubed.com!
#Forensics #DigitalForensics #DFIR #macOSForensics
https://www.youtube.com/watch?v=_D6oHm-371A
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Offensive Security Web Expert (OSWE) Review + Tips/Tricks [OffSec]
Offensive Security Web Expert (OSWE) review, tips/tricks etc. Hopefully this video will be useful for aspiring bug bounty hunters, security researchers, pentesters, CTF players etc who might be interested in taking the Advanced Web Attacks and Exploitation course from Offensive Security (OffSec) 🙂 #OSWE #BugBounty #EthicalHacking #PenTesting #AppSec #WebSec #InfoSec #OffSec
↢OffSec OSWE↣
Web-300 course: https://www.offsec.com/courses/web-300
Web-300 syllabus: https://manage.offsec.com/app/uploads/2023/01/WEB-300-Syllabus-Google-Docs.pdf
Web-300 FAQ: https://help.offsec.com/hc/en-us/articles/360046868971-WEB-300-Advanced-Web-Attacks-and-Exploitation-FAQ
OSWE exam guide: https://help.offsec.com/hc/en-us/articles/360046869951-WEB-300-Advanced-Web-Attacks-and-Exploitation-OSWE-Exam-Guide
OSWE...
https://www.youtube.com/watch?v=IK4t-i5lDEs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTVcron: Introduction to Ghidra and Version Tracking
RTVcron is our monthly live stream where we bring workshops to you! Learn more about cron and RTV at https://redteamvillage.io
Mike will demonstrate basic Ghidra functionality such as importing programs, launching tools, and using the standard windows and plugins. Next he will explain the design and use of the Version Tracking tool, and how it can help your workflow understanding functionality while analyzing upgrades to software.
Finally, time permitting, he will show beginning usage of the BSim capability and how this can be a game changer for discovering lineage of software en masse.
Participants are encouraged to ask questions about the application, as Mike will be demonstrating everything live without a net.
https://www.youtube.com/watch?v=6ou3Qcwuao8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Vibe Coding in Cursor for Cyber Security
In the past few weeks I've dove headfirst into vibe coding with Cursor, so I wanted to share what I've been working on and some tips and tricks. In this video we'll cover all things vibe coding for hackers: What is it? How is it making waves on Twitter and within the startup and AI influencer communities? More importantly, what does it mean for us bug bounty hunters and hackers? I'll share tips on using AI for coding, how to get started with tools like Cursor, Gemini, and Docker, and even give you a peek at a vibe-coded pet adoption website I worked on. Whether you're a coding newbie or looking to simplify your process, this video has something for you. Enjoy!
Links:
Awesome .cursorrules: https://github.com/PatrickJS/awesome-cursorrules
Spec-drive Vibe Coding (how to write design docs for...
https://www.youtube.com/watch?v=wnVpmSrhNRo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
A New(ish) Way to Detect Process Hollowing
In this episode, we'll briefly explore how process hollowing works. Then, we'll examine the relatively new windows.hollowprocesses plugin for Volatility 3—a more recent alternative to the popular HollowFind plugin from Volatility 2. As you'll see, this new plugin isn't a one-for-one replacement for HollowFind, but it can still be useful.
⚠️ Deprecation Notice
The windows.hollowprocesses plugin is being renamed to windows.malware.hollowprocesses in an upcoming Volatility 3 release. The plugin's behavior and output remain unchanged.
❤️ Special thanks to Mike Peterson of https://nullsec.us for research and testing.
Download the memory samples here:
https://cdn.13cubed.com/downloads/hollow.zip
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed....
https://www.youtube.com/watch?v=x5mGPAG41I4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tsuku CTF Web Challenge Walkthroughs (2025)
🚩 Video walkthrough for the 3 web challenges featured in the 2025 Tsuku CTF competition. Challenges include JSON injection, sensitive file disclosure and flawed PRNG implementation, YAML injection with WAF 😎 #CTF #Challenge #Tsuku
Check out the accompanying writeups here: https://cryptocat.me/blog/ctf/2025#tsuku
Join my discord server if you have any questions: https://discord.cryptocat.me
🐛CIT@CTF🐞
https://tsukuctf.org
https://discord.gg/xNgh3a6Ynp
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00 Intro
0:08 len_len
2:47 flash
8:28 YAMLwaf
12:23 Conclusion
https://www.youtube.com/watch?v=qGd4d0zmhy8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
CTF@CIT Web Challenge Walkthroughs (2025)
🚩 Video walkthrough for the 5 web challenges featured in the 2025 CIT@CTF competition. Challenges include SQL injection (SQLi), git repo version history (git-dumper), local file read (with basic filter), flask session cookie tampering + server-side template injection (SSTI) and credential reuse / HTTP method tampering 😎 #CTF #Challenge #CIT
Check out the accompanying writeups here: https://cryptocat.me/blog/ctf/2025/#ctf-cit
Join my discord server if you have any questions: https://discord.cryptocat.me
🐛CIT@CTF🐞
https://ctf.cyber-cit.club
https://discord.gg/GzUAsFvhbk
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00 Intro
0:06 Breaking authentication (SQLi)
2:20 Commit & Order: Version Control Unit (git dumping / history)
4:25 How I Parsed your JSON...
https://www.youtube.com/watch?v=ZBdApaw0r0M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTVcron | Systematic Malware: A Rule-Based Approach to Creating Payloads
RTVcron is our monthly live stream where we bring workshops to you! Learn more about cron and RTV at https://redteamvillage.io
This month we're joined by Kevin Clark and Skyler Knecht for "Systematic Malware: A Rule-Based Approach to Creating Payloads"
Creating evasive payloads in the modern EDR landscape is less about knowing what to do, and more about learning what not to do. Although EDR has moved away from relying on static binary signatures, rule-based detections are still in play. Every step of payload execution is an opportunity to be detected. In this workshop, we showcase step-by-step instructions on how to craft evasive payloads.
Kevin Clark
Security Consultant at TrustedSec
Kevin Clark is a Software Developer turned Penetration Tester at TrustedSec. He focuses on initial access...
https://www.youtube.com/watch?v=-xStGweK9KI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Reverse Engineering Access Tokens Part 2
This tutorial covers Windows Access Tokens, the Logon Session, Token Elevation, AdjustTokenPrivileges and the Windows Access Control Model.
This is part of our IDA Pro reverse engineering series. The full series can be found on our patron...
https://www.patreon.com/collection/1259251
-----
References
Token Viewer (Tool)
https://github.com/googleprojectzero/sandbox-attacksurface-analysis-tools
LogonSessions (Tool)
https://learn.microsoft.com/en-us/sysinternals/downloads/logonsessions
Elastic - Introduction to Windows tokens for security practitioners
https://www.elastic.co/blog/introduction-to-windows-tokens-for-security-practitioners
UAC Overview (old but good)
https://www.tiraniddo.dev/2017/05/reading-your-way-around-uac-part-1.html
Access Control Model (Microsoft)
https://learn.microsoft.com/en-us/windows/win32/secauthz/access-control-components
LSA...
https://www.youtube.com/watch?v=Y58eBWyJxDA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Getting Started with Fuji - The Logical Choice for Mac Imaging
In this episode, we'll look at Fuji—a free, open-source tool for performing live, logical forensic acquisitions of Mac computers (Intel or Apple Silicon). You'll see how Fuji leverages built-in macOS tools to generate a DMG and sparseimage, ready for analysis in your forensic tool of choice.
This video is an excerpt from the 13Cubed training course "Investigating macOS Endpoints." Visit https://training.13cubed.com to learn more!
🛠 Resources
Fuji:
https://github.com/Lazza/Fuji
https://www.youtube.com/watch?v=9bEiizjySHA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How FIN6 Exfiltrates Files Over FTP
Access the FIN6 Exfiltration Lab: https://bit.ly/3XsXFRZ
In this final episode of our FIN6 Adversary Emulation mini-series, we demonstrate how to emulate FIN6's exfiltration techniques, focusing on how this financially motivated threat actor collects, stages, archives, and exfiltrates sensitive data from compromised systems.
// CYBER RANGES Adversary Emulation Labs
► New to CYBER RANGES? Register for a free account here: https://bit.ly/42VxDu5
► Access the FIN6 Exfiltration Lab: https://bit.ly/3XsXFRZ
► Adversary Emulation Fundamentals Labs (Free): https://bit.ly/4gQd8SB
🔗 Video Resources & References
CTID Adversary Emulation Library: https://github.com/center-for-threat-informed-defense/adversary_emulation_library
🎥 Have an idea for a video? make your submission here: https://forms.gle/VDwwMsuudzQfT9VM6
//...
https://www.youtube.com/watch?v=SbZ7JUII-SQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
From Zero to Zero Day (and beyond) - Life of a Hacker: Jonathan Jacobi
I met Jonathan in 2018 at the CCC when he was just 18 years old. Back then he referenced my videos which had a little bit of impact on his life. Now a lot of time has passed and in this interview I want to get to know Jonathan better. How did he get into hacking, founding of the CTF team perfect blue, working as a vulnerability researcher and ultimately transitioning into a new career.
From Zero to Zero Day (2018): https://www.youtube.com/watch?v=xp1YDOtWohw
Jonathan on Twitter: https://x.com/j0nathanj
00:00:00 - How we met
00:02:16 - Jonathan's early life
00:04:24 - Going to college as a teenager
00:18:52 - Meeting like-minded people in CTF
00:27:29 - Getting first VR internship at Checkpoint
00:32:34 - Creating opportunities through networking
00:43:40 - Working at Microsoft Security Response...
https://www.youtube.com/watch?v=BOLN_B0qnZk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Automated AI Reverse Engineering with MCP for IDA and Ghidra (Live VIBE RE)
Testing MCP plugins for IDA and Ghidra live with @mrexodia
IDA MCP
https://github.com/mrexodia/ida-pro-mcp
Ghidra MCP (thanks @lauriewired )
https://github.com/LaurieWired/GhidraMCP
Malware sample
7b5b060d9013725413f3f77719d0881035246b281e18005c0040e78a32e1c6cc
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=iFxNuk3kxhk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTVcron - Influcence_Ops: Tactical Pretexting
Welcome to RTVcron, our monthly live stream, held on the last Thursday of every month. Each two-hour session features a unique workshop led by a different expert, offering hands-on experience in offensive security tactics and strategies.
Follow us: https://redteamvillage.io
This month our workshop is provided by Jeff Tomkiewicz!
Jeff Tomkiewicz is a Offensive Security Engineer for a Healthcare Fortune 40 organization, where he specializes in network penetration testing, social engineering, and physical penetration testing. With a rich background as a 21-year Air Force veteran, Jeff has served in various capacities, including K9 handler and trainer, Intelligence, and Special Operations. Residing in Colorado Springs, CO, where interests span upon horror films, performing in improv shows,...
https://www.youtube.com/watch?v=vlow4qZSOSE
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Reverse Engineering Access Tokens Part 1
This tutorial walks through the process of reverse engineering malware which uses AdjustTokenPrivileges to enable SeDebugPrivilege. No steps are skipped in the process!
This is Module 2.2 of our IDA Pro reverse engineering series. The full series can be found on our patron...
https://www.patreon.com/collection/1259251
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=iT2U3UXhic4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 0. Introduction
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=1AAZDkSZePs
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 11 - Additional Resources and Personal Message
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=zVgV__cRhvo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 10 - Finding Hidden Wireless Networks with Python
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=0EB5U8dcAVc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 9 - Spoofing your MAC Address with Python
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=OtvSfjX6kGY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 8 - Cracking Hashes with Python and Hashlib
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=EA4JFh8hj9E
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 7 - Discovering Subdomains with Python
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=X9oyU7kUob8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 6 - Attacking Web Forms with requests and BeautifulSoup in Python
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=sYg3dyetcYA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Python for Pentesters II - 5 - The Scapy Module for Network Traffic Sniffing and Manipulation
Part of the Python for Pentesters II course: https://www.youtube.com/playlist?list=PLonlF40eS6nyj9h8wwrOgf1yBGDB2CYT1
Connect with me:
X: https://twitter.com/cristivlad25
IG: https://instagram.com/cristivladz
https://www.youtube.com/watch?v=M_5YKbsk4eY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
18 - API Security (low/med/high) - Damn Vulnerable Web Application (DVWA)
18 - API Testing (low/med/high difficulties) video from the Damn Vulnerable Web Application (DVWA) walkthrough/tutorial series. DVWA is an intentionally vulnerable application for you to learn about ethical hacking. I made this series for students on the MSc in cybersecurity course at Queen's University Belfast but hopefully it can help others too! Hope you enjoy 🙂
↢Damn Vulnerable Web Application (DVWA)↣
https://github.com/digininja/DVWA
👷♂️Resources🛠
https://cryptocat.me/resources
↢Chapters↣
Start - 0:00
Low - 0:38
Med - 3:59
High - 7:07
Impossible - 13:19
End - 13:35
https://www.youtube.com/watch?v=c_6RaCekH40
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The German Hacking Championship
An amazing event for aspiring German hackers is happening right now. I went to the finals in 2024, share a few impressions and tell you about this year's event.
Learn hacking: https://www.hextree.io/ (ad)
CSCG 2025 runs from 1. March 2025 until 1. May 2025
Rules: https://play.cscg.live/rules
Die Hacking Meisterschaft: https://hacking-meisterschaft.de/
NFITS: https://nfits.de/spenden/
European Cybersecurity Challenge: https://ecsc.eu/
00:00 - Intro DHM 2024
00:52 - CTF Teams vs. CSCG Teams
01:48 - Sponsor Challenges
03:04 - My CSCG History
04:18 - NFITS
05:06 - Die Deutsche Hacking Meisterschaft (DHM)
07:00 - Take the Opportunity!
07:47 - Outro
=[ ❤️ Support ]=
→ My courses: https://www.hextree.io/
→ My font: https://shop.liveoverflow.com/
→ per Video: https://www.patreon.com/join/liveoverflow
→...
https://www.youtube.com/watch?v=f0C3RH7baEw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
17 - Cryptography (low/med/high) - Damn Vulnerable Web Application (DVWA)
17 - Cryptography (low/med/high difficulties) video from the Damn Vulnerable Web Application (DVWA) walkthrough/tutorial series. DVWA is an intentionally vulnerable application for you to learn about ethical hacking. I made this series for students on the MSc in cybersecurity course at Queen's University Belfast but hopefully it can help others too! Hope you enjoy 🙂
↢Damn Vulnerable Web Application (DVWA)↣
https://github.com/digininja/DVWA
↢Cryptography↣
https://cryptohack.org
@pastiesbin2254 : https://www.youtube.com/watch?v=8Tr2aj6JETg
https://www.nccgroup.com/uk/research-blog/cryptopals-exploiting-cbc-padding-oracles
@nccgroup : https://www.youtube.com/watch?v=6yHM19rQjDo
👷♂️Resources🛠
https://cryptocat.me/resources
↢Chapters↣
Start - 0:00
Low - 0:14
Med...
https://www.youtube.com/watch?v=7WySPRERN0Q
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTV Overflow: "Breaching Bare Metal Kubernetes Clusters" with Graham Helton
Graham Helton - Arbiter of (in scope) chaos - "Attackers thrive in complex environments because they're motivated to dive deep into ambiguous technical details. In this workshop I will guide you through those ambiguous technical details by walking through multiple attack scenarios that can be used to fully compromise a bare metal Kubernetes cluster.
After each attack, we'll discuss controls that could stop or mitigate each attack, what tools you should carry in your toolbox when performing a Kubernetes assessment, and the security implications (and misconceptions) of Kubernetes. By the end of this workshop, you will be paranoid by the power you possess next time you land a shell in a Kubernetes pod."
Web: https://grahamhelton.com/
Twitter/X: @GrahamHelton3
linkedin.com/in/grahamhelton/
...
https://www.youtube.com/watch?v=iR064xsllqk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTV Overflow "An Operators Guide: Hunting SCCM in the Real World" w/ Zachary Stein & Garrett Foster
Zachary Stein (Security Consultant at SpecterOps) and Garrett Foster (Senior Security Consultant at SpecterOps) - "SCCM abuse has become a popular technique in the offensive security community but can be intimidating to test in production environments due to its complexity. This workshop aims to provide operators not only a safe environment to practice tradecraft but also provide them with the confidence to properly find and assess SCCM during their engagements."
Twitter/X: @unsigned_sh0rt
Twitter/X: @synzack21
https://www.linkedin.com/in/garrett-foster86/
https://www.linkedin.com/in/zacharydstein/
________________________________________________________________
The Red Team Village
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter:...
https://www.youtube.com/watch?v=TmfWYDqEEUo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTV Overflow: "Physical Red Teaming for Offensive Cyber Teams" with Ana Aslanishvili & Shawn Abelson
Ana Aslanishvili (Red Teaming Aficionado) and Shawn Abelson (Ex-Head of Physical Red Team @ Meta, Current Consultant/Trainer for PhySec Red Teaming) - "Offensive security is an unfamiliar concept to most physical security practitioners. Yet we still rely on physical security teams to protect our hardware, network, ports, and assets. Physical security professionals are often non-technical, former law enforcement/military, and are focused on protecting people instead of property. This talk will bridge the gap between physical and cyber red teaming, covering the best approaches, common pitfalls, dangers, and benefits of testing physical security programs as part of a red team assessment. From the difficulty of “patching” physical vulnerabilities to examples of red teams gone wrong and how...
https://www.youtube.com/watch?v=FZS32kb5IXk
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Do you know this common Go vulnerability?
When auditing code it's crucial to know about common issues. In this video we explore a Go issue that I was not aware of.
Learn hacking on https://www.hextree.io/ (ad)
38c3 CTF - Fajny Jagazyn Wartości Kluczy:
https://2024.ctf.link/internal/challenge/fb03748d-7e94-4ca2-8998-a5e0ffcbd761/
Unintended solution: https://msanft.foo/blog/hxp-38c3-web-fajny-jagazyn/
Challenge author writeup: https://hxp.io/blog/114/hxp-38C3-CTF-Fajny-Jagazyn-Wartoci-Kluczy/
VSCode Go debugger client code: https://github.com/golang/vscode-go/blob/39786ea90f18ab98f75d091b9a04367d1b1df82c/extension/src/debugAdapter/goDebug.ts#L1557
00:00 - Intro
00:20 - Go gjson vs json behavior
01:33 - Overview CTF challenge "Fajny Jagazyn Wartości Kluczy"
04:33 - Weird server setup?
05:55 - Arbitrary file read
07:00 - /proc...
https://www.youtube.com/watch?v=wVknDjTgQoo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RADAR Contact! An Obscure Evidence of Execution Artifact
In this episode, we'll take a look at a rather obscure evidence of execution artifact associated with RADAR, the Resource Exhaustion Detection and Resolution system.
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
01:16 - What You Need to Know
🛠 Resources
The Mystery of the HeapLeakDetection Registry Key:
https://harelsegev.github.io/posts/the-mystery-of-the-heapleakdetection-registry-key/
HeapLeakDetection Registry Forensics:
https://github.com/MHaggis/HeapLeakDetection
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics
https://www.youtube.com/watch?v=edJa_SLVqOo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Emulating FIN6 - Active Directory Enumeration Made EASY
In this episode of the FIN6 Adversary Emulation series, we focus on Active Directory (AD) enumeration—a critical phase in FIN6's discovery techniques. Understanding how adversaries enumerate Active Directory environments will help you refine your tradecraft or improve your detection and mitigation capabilities if you are a Blue Teamer.
In this video, you will learn how FIN6 performs Active Directory enumeration, and how to use native Windows commands like "net" and PowerShell's "Get-AD*" cmdlets for AD Enumeration. You will also learn how to utilize "AdFind.exe" to extract information from an Active Directory Environment.
The lab environment used in this demonstration is available for free on CYBER RANGES, allowing you to follow along and practice these techniques in a safe and controlled...
https://www.youtube.com/watch?v=Iwxmscx3XXc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
A Scammer Tried to Hack Me!
🚨🚔 I was recently offered a video sponsorship opportunity which turned out to be a DocuSign scam! They said they liked my videos but really just wanted to infect me with some malware 😿 Anyway, I thought I'd make a quick educational video to raise awareness. I'll explain what raised my suspicions and how I confirmed that the scammer was trying to hack me! #MalwareAnalysis #CyberSecurity #CyberSecurityAwareness #InfoSec #ScamBaiting #CryptoCat
🦠Malware Analysis🦠
VirusTotal: https://www.virustotal.com/gui/file/8f6f207277a8881e9c2042de4dc3a7c824eaa0334f522d96d412a2dfe5f93820/detection
APP.ANY.RUN Analysis: https://app.any.run/tasks/78722395-a017-4ac5-a18c-47464aae63a7
APP.ANY.RUN Safebrowsing: https://app.any.run/browses/6a13f769-5ec1-43e4-bc23-71f076e04e36
DocuSign Scams: https://abnormalsecurity.com/blog/cybercriminals-exploit-docusign
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00...
https://www.youtube.com/watch?v=v8ZwlKAjMJA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The SECRET to Embedding Metasploit Payloads in VBA Macros
In this episode of the Offensive VBA series, we explore how to integrate PowerShell payloads and stagers into custom VBA macros for initial access. Specifically, we'll demonstrate how to repurpose and format PowerShell stagers generated by Msfvenom and PowerShell-Empire to execute a reverse shell.
This video will teach you how to format and embed HTA-based PowerShell payloads inside a VBA macro.
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
🎥 Have an idea for a video? make your submission here: https://forms.gle/VDwwMsuudzQfT9VM6
// MORE RESOURCES
HACKERSPLOIT BLOG ►► https://bit.ly/3qjvSjK
HACKERSPLOIT FORUM ►► https://bit.ly/39r2kcY
HACKERSPLOIT ACADEMY ►►...
https://www.youtube.com/watch?v=Q1wQuHw5JKI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
RTV Overflow
RTV Overflow is a full-day virtual event packed with some of your favorite workshops from DEFCON 32!
Starting at 10:00 AM ET, the event features hands-on workshops including sessions on breaching Kubernetes clusters, physical red teaming strategies, and advanced cloud exploitation techniques. Get a behind-the-scenes look at RTV's mission, learn how our CTF comes to life, and discover opportunities to contribute to the village at the upcoming DEF CON 33. With sessions led by top professionals this event is your gateway to mastering real-world red team techniques and connecting with the global offensive security community.
Visit redteamvillage.io to learn more about our mission and sign up!
https://www.youtube.com/watch?v=JMTMEEqaBKg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Offensive VBA 0x4 - Reverse Shell Macro with Powercat
In this episode of the Offensive VBA series, we dive into one of the most powerful techniques for red teamers—creating a reverse shell VBA macro using Powercat. This technique enables stealthy command execution and remote access through malicious macro-enabled Office documents.
In this video, you will learn how to build a reverse shell VBA Macro that leverages Powercat allowing you to stealthily execute remote commands in-memory using PowerShell.
Powercat: https://github.com/besimorhino/powercat
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
🎥 Have an idea for a video? make your submission here: https://forms.gle/VDwwMsuudzQfT9VM6
// MORE RESOURCES
HACKERSPLOIT BLOG ►►...
https://www.youtube.com/watch?v=0W3Z3Br56XM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Offensive VBA 0x3 - Developing PowerShell Droppers
In this episode of the Offensive VBA series, we take VBA macros to the next level by developing PowerShell droppers designed for red team operations. Learn how to craft stealthy and effective VBA scripts that deliver and execute PowerShell payloads seamlessly.
Here's what we'll cover: Writing VBA macros to execute PowerShell scripts, executing payloads directly in memory for stealth, leveraging environment variables to identify system paths dynamically, and techniques to remove traces of macro execution for stealthier operations
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
🎥 Have an idea for a video? make your submission here: https://forms.gle/VDwwMsuudzQfT9VM6
// MORE...
https://www.youtube.com/watch?v=ot3053UxJOc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Offensive VBA 0x2 - Program & Command Execution
Welcome to the second episode of the Offensive VBA series, where we explore how to execute programs and system commands using VBA macros—essential skills for red teamers looking to leverage VBA for initial access and automation.
In this video, you will learn how to use the Shell function to run external programs and commands and leverage the WScript.Shell object for enhanced control over command execution. You will also learn how to use the Shell Window Style options to ensure stealth during execution.
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
🎥 Have an idea for a video? make your submission here: https://forms.gle/VDwwMsuudzQfT9VM6
// MORE RESOURCES
HACKERSPLOIT BLOG...
https://www.youtube.com/watch?v=ogbrNZ3SCRY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Offensive VBA 0x1 - Your First Macro
Welcome to the first episode of the Offensive VBA series, where we equip red teamers with the skills to leverage VBA for initial access and offensive operations. This video introduces you to Visual Basic for Applications (VBA)—a powerful scripting language integrated into Microsoft Office.
Here's what we'll cover: What is VBA?: An overview of how VBA works and integrates with MS Office, A walkthrough of the Integrated Development Environment (IDE) and its features, and How to create and run a basic macro.
Core Concepts:
- Subroutines, Functions, and their calls.
- Variable declaration, data types, and scope.
- User input/output with MsgBox and control statements.
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation...
https://www.youtube.com/watch?v=jGy7_NusjuQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Emulating FIN6 - Gaining Initial Access (Office Word Macro)
Welcome to the next installment in our adversary emulation series! This video focuses on emulating initial access via a spear-phishing attachment—specifically, a malicious Word document with an embedded macro, just like FIN6 might use.
🚨 Next Up: If you want to manually develop your own VBA macros for initial access, don't worry—we've got you covered in the next video, where we'll dive deeper into crafting custom macros for red team operations.
🎥 Practical Labs: This video uses the CYBER RANGES platform to simulate a realistic attack environment. Try it out and follow along!
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
The lab used in this video: https://app.cyberranges.com/scenario/624cd3877733a30007185a15
🔗...
https://www.youtube.com/watch?v=hUBRnh5dzrI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
USB Ethernet Adapter Malware??? Chinese RJ45-USB Full Analysis - Part 1
Reverse engineering all stages with line by line code analysis.
e3f57d5ebc882a0a0ca96f9ba244fe97fb1a02a3297335451b9c5091332fe359
OP
https://epcyber.com/blog/f/chinese-rj45-usb-with-flash-memory-exe-recognized-as-malware
--
OALABS PATREON
https://www.patreon.com/oalabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
https://www.youtube.com/watch?v=3IfJSGWIrCo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
FIN6 Adversary Emulation Plan (TTPs & Tooling)
Step into the world of adversary emulation with this in-depth video on the FIN6 Emulation Plan. Learn how to use the Center for Threat-Informed Defense (CTID) Adversary Emulation Library to craft a comprehensive emulation plan that replicates FIN6's sophisticated TTPs.
This video will provide you with: An intelligence summary of FIN6, and the FIN6 emulation plan detailing TTPs from initial access to discovery, privilege escalation, and exfiltration.
The Adversary Emulation Fundamentals labs used in this video and series are available for free on CYBER RANGES to practice and refine your emulation skills.
// Adversary Emulation Labs
New to CYBER RANGES? Register here: https://bit.ly/40dRMsb
CYBER RANGES Adversary Emulation Labs (Free): https://bit.ly/4amBPEU
Lab used in this video: https://app.cyberranges.com/scenario/624cb3bd7733a30007185990
🔗...
https://www.youtube.com/watch?v=qEfk44G4zFM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Developing An Adversary Emulation Plan
Creating an adversary emulation plan is a critical process for red teamers and cybersecurity professionals aiming to improve their organization's threat detection and response capabilities. In this video, we break down the entire process starting with how to select a threat actor relevant to your industry or geolocation, finding and leveraging Cyber Threat Intelligence (CTI) to gather insights on the adversary, and mapping the adversary's TTPs using the MITRE ATT&CK framework.
🔗 Video Resources & References
Explore the comprehensive APT Groups and Operations Directory to find details on APT groups by region, their TTPs, and campaigns: https://apt.threattracking.com
APTnotes: https://github.com/kbandla/APTnotes
APT & CyberCriminal Campaign Collection: https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections
//...
https://www.youtube.com/watch?v=1N49x1EWw7s
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How 3 Hackers Combined Their Skills for Big Bounties! (And how you can do it too)
Join us in this special episode as we sit down with the winners of Bugcrowd's Hacker Showdown Carnival of Chaos virtual event: sw33tLie, bsysop, and godiego! Discover their hacking methodologies, collaboration techniques, and their journey to victory. Learn how they met, their advice for forming your own team, and the coolest exploits they uncovered during the event. If you're interested in bug bounties, team hacking, or just want to meet more hacker friends, this episode is a must-watch!
00:00 Introduction and Special Guests
01:04 Meet the Hackers
02:55 Carnival of Chaos Experience
04:32 Collaboration and Team Dynamics
06:15 Roles and Strategies in Hacking
13:00 Finding the Right Collaborators
15:25 Live Hacking Events vs. Virtual Events
22:30 Coolest Findings and Bug Stories
29:52 Advice...
https://www.youtube.com/watch?v=gUuDyIE44bc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction To Advanced Persistent Threats (APTs)
This informative video is designed to give you a comprehensive understanding of Advanced Persistent Threats (APTs). In this video, you will learn what APTs are, how they differ from traditional threat actors, and why they pose a significant challenge to organizations worldwide. This video also explores the categorization and naming of APT Groups based on nation-state affiliation, motivations, and the tactics they employ to achieve their objectives.
This video also sheds light on the complexities of APT naming conventions used by major cybersecurity vendors, such as CrowdStrike and Mandiant, and the challenges in tracking these elusive groups.
🔗 Don't miss this resource: Access the "APT Groups and Operations" repository here: https://apt.threattracking.com — a comprehensive spreadsheet...
https://www.youtube.com/watch?v=CwSG5sa0Nao
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Be Kind, Rewind... The USN Journal
In this episode, we'll explore groundbreaking research from CyberCX on “rewinding the NTFS USN Journal.” This innovative technique reveals how to uncover the original locations of files recorded in the USN Journal, even after their corresponding NTFS FILE records have been reused by different files.
🛑 If you need a refresher on the prerequisites for this episode, watch these:
Introduction to MFTECmd - NTFS MFT and Journal Forensics:
https://www.youtube.com/watch?v=_qElVZJqlGY
Anatomy of an NTFS FILE Record - Windows File System Forensics:
https://www.youtube.com/watch?v=l4IphrAjzeY
NTFS FILE Record Reuse:
https://www.youtube.com/watch?v=6LpJVx7PrUI
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
05:03...
https://www.youtube.com/watch?v=GDc8TbWiQio
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
403 Bypass and Deserialization in BentoML Library (CVE-2024-2912) - "Summar-AI-ze" [Web Challenge]
🚩 Video walkthrough for the "Summar-AI-ze" (web) challenge I created and hosted on my NEW website (https://cryptocat.me)!! Players were required to bypass a 403 error by using the X-Forwarded-For HTTP header, allowing them to activate an internal feature and grant their account beta access. The "beta" feature was a word summarization tool, running BentoML (LLM) on the backend. Players could identify the library by changing the content-type, triggering an error. Some research would yield CVE-2024-2912; a python pickle deserialization vulnerability, discovered by PinkDraconian 💜 Players could use the supplied PoC to gain code execution and exfiltrate the flag using curl 😎 #CTF #Challenge #CryptoCat
Check out the accompanying writeup here: https://cryptocat.me/blog/ctf/monthly/cryptocat/1224/summaraize/
Join...
https://www.youtube.com/watch?v=5NCzDZcx_Dg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Advent of Cyber Day 24: MQTT & Wireshark
Check out TryHackMe's Advent of Cyber Event: https://tryhackme.com/r/christmas?utm_source=youtube&utm_medium=social&utm_campaign=
Join Katie, aka InsiderPhD, on the 24th day of TryHackMe's Advent of Cyber! Today, we're diving into the mysterious world of communication protocols, focusing on the MQTT protocol. Discover how the city of Wereville faces off against Mayor Malware's sabotage of smart lights and HVAC systems. Using Wireshark, Katie demonstrates how to analyze MQTT traffic, understand the publish-subscribe model, and reverse engineer networking protocols. With a blend of British humour and hands-on learning, Katie leads you through the process of identifying malicious commands and securing IoT devices. By the end, you'll learn how to troubleshoot smart devices, monitor network...
https://www.youtube.com/watch?v=ct6393M_Iow
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction To Adversary Emulation
This video introduces you to Adversary Emulation and its role in Red Team operations. Furthermore, this video also explains the differences between Adversary Emulation and Simulation. Adversary emulation in the context of Red Teaming is the process of mimicking/emulating the tactics, techniques, and procedures (TTPs) of a threat actor/adversary to test the effectiveness and efficacy of an organization's defenses.
//PLATFORMS
BLOG ►► https://bit.ly/3qjvSjK
FORUM ►► https://bit.ly/39r2kcY
ACADEMY ►► https://bit.ly/39CuORr
//SOCIAL NETWORKS
TWITTER ►► https://bit.ly/3sNKXfq
DISCORD ►► https://bit.ly/3hkIDsK
INSTAGRAM ►► https://bit.ly/3sP1Syh
LINKEDIN ►► https://bit.ly/360qwlN
PATREON ►► https://bit.ly/365iDLK
MERCHANDISE ►► https://bit.ly/3c2jDEn
//BOOKS
Privilege...
https://www.youtube.com/watch?v=CUMhiSdOSkY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Advent of Cyber Day 13: Exploring WebSocket Vulnerabilities with InsiderPhD
Check out TryHackMe's Advent of Cyber Event: https://tryhackme.com/r/christmas?utm_source=youtube&utm_medium=social&utm_campaign=
Join me, in today's TryHackMe Advent of Cyber Day 13 walkthrough, where she diving into WebSockets and WebSocket message manipulation vulnerabilities. Learn about WebSocket message manipulation, common security risks such as weak authentication, message tampering. Follow along as I demonstrates how to identify and exploit WebSocket vulnerabilities in a web application. Perfect for anyone interested in web security, bug bounty hunting, and real-time communication protocols.
00:00 Introduction and Welcome
00:26 Story Setup: The Threat in Wareville
01:22 Understanding WebSockets
02:54 WebSocket Vulnerabilities
04:08 WebSocket Message Manipulation
07:33 Practical...
https://www.youtube.com/watch?v=ozgRXn44FF0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Mastering Persistence: Using an Apache2 Rootkit for Stealth and Defense Evasion
In this video, I demonstrate the process of establishing persistence and evading defenses on Linux through the use of an Apache2 rootkit.
The lab used in this video can be accessed for free on the CYBER RANGES platform. The links to the platform and lab are listed below:
// CYBER RANGES
CYBER RANGES: https://app.cyberranges.com
SQL Injection Lab: https://app.cyberranges.com/scenario/67474e64a3907f65136f1a6d
//LINKS
Apache2 Rootkit: https://github.com/ChristianPapathanasiou/apache-rootkit
//PLATFORMS
BLOG ►► https://bit.ly/3qjvSjK
FORUM ►► https://bit.ly/39r2kcY
ACADEMY ►► https://bit.ly/39CuORr
//SOCIAL NETWORKS
TWITTER ►► https://bit.ly/3sNKXfq
DISCORD ►► https://bit.ly/3hkIDsK
INSTAGRAM ►► https://bit.ly/3sP1Syh
LINKEDIN ►► https://bit.ly/360qwlN
PATREON...
https://www.youtube.com/watch?v=Ra2altDvPYI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
XSS via CSPT and DOM Clobbering - "SafeNotes 2.0" [INTIGRITI 1337UP CTF 2024]
🚩 Video walkthrough for the "Safe Notes 2.0" (web) challenge I made for @intigriti's 1337UP LIVE (CTF) competition 2024! The developer of Safe Notes learnt from their mistakes and introduced a variety of security fixes, but unfortunately introduced new vulnerabilities! Players were required to chain DOM Clobbering, client-side path traversal (CSPT) and an Open Redirect in order to achieve XSS and steal the admin's cookie. 😎 #1337UP #1337UPLIVE #CTF #INTIGRITI #HackWithIntigriti
Check out the accompanying writeup here: https://cryptocat.me/blog/ctf/2024/intigriti/web/safenotes_2
Check out Safe Notes v1 challenge and walkthrough here: https://challenge-0824.intigriti.io + https://youtu.be/yGRRGUtT9MU
🐛INTIGRITI 1337UPLIVE CTF🐞
https://ctftime.org/event/2134
https://ctf.intigriti.io
https://discord.gg/intigriti-870275171938873395
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00...
https://www.youtube.com/watch?v=G-KoF8WAoUM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
NTFS FILE Record Reuse
In this continuation of "Anatomy of an NTFS FILE Record," we'll learn how NTFS manages record reuse and distinguishes between in-use and deleted files and directories.
If you haven't watched the previous episode, watch it here:
https://www.youtube.com/watch?v=l4IphrAjzeY
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
00:31 - NTFS Master File Table (MFT) artiFACTS
01:49 - Analysis
#Forensics #DigitalForensics #DFIR #ComputerForensics #WindowsForensics
https://www.youtube.com/watch?v=6LpJVx7PrUI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Basic Stack Buffer Overflow (with parameters) - "Retro2Win" [INTIGRITI 1337UP CTF 2024]
🚩 Video walkthrough for the "Retro2Win" (pwn) challenge I made for @intigriti's 1337UP LIVE (CTF) competition 2024! A classic "ret2win" challenge, the binary included a buffer overflow vulnerability, allowing players to take over the flow of execution and call a "win" function. In this case, the function expected two parameters, requiring values to be popped into the RDI/RSI registers first 😎 #1337UP #1337UPLIVE #CTF #INTIGRITI #HackWithIntigriti
Check out the accompanying writeup here: https://cryptocat.me/blog/ctf/2024/intigriti/pwn/retro2win
🐛INTIGRITI 1337UPLIVE CTF🐞
https://ctftime.org/event/2134
https://ctf.intigriti.io
https://discord.gg/intigriti-870275171938873395
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00 Intro
0:13 Basic file checks
0:50...
https://www.youtube.com/watch?v=Y37KMst1XFU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
X-Forwarded-For Header Spoofing and XXE - "BioCorp" [INTIGRITI 1337UP CTF 2024]
🚩 Video walkthrough for the "BioCorp" (web) challenge I made for @intigriti's 1337UP LIVE (CTF) competition 2024! Players arrived an a website for an energy corporation, with a hint that they were working on decoupling their backend infrastructure from the public facing website. By analysing the source code, players would find a hidden panel, restricted by IP address. By setting the X-Forwarded-For header, they could spoof the IP and gain access to a nuclear panel. Since the panel read XML data, players would test for XXE and ultimately recover the flag 😎 #1337UP #1337UPLIVE #CTF #INTIGRITI #HackWithIntigriti
Check out the accompanying writeup here: https://cryptocat.me/blog/ctf/2024/intigriti/web/biocorp
🐛INTIGRITI 1337UPLIVE CTF🐞
https://ctftime.org/event/2134
https://ctf.intigriti.io
https://discord.gg/intigriti-870275171938873395
👷♂️Resources🛠
https://cryptocat.me/resources
Overview:
0:00...
https://www.youtube.com/watch?v=hyi_JZvXOTU
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
13Cubed XINTRA Lab Walkthrough
In this episode, we'll perform a comprehensive walkthrough of the 13Cubed challenge created for XINTRA Labs. Learn more at https://www.xintra.org/labs.
💰 For a limited time only, use the discount code "13CUBED" to get 15% off a XINTRA Labs subscription!
🙏 Special thanks to Mike Peterson from https://nullsec.us for playing the role of Threat Actor in our scenario!
*** If you enjoy this video, please consider supporting 13Cubed on Patreon at patreon.com/13cubed. ***
📖 Chapters
00:00 - Intro
00:58 - Workstation - Running MemProcFS
03:25 - Workstation - Question 1
05:14 - Workstation - Question 2
07:06 - Workstation - Question 3
07:53 - Workstation - Question 4
09:42 - Workstation - Question 5
12:42 - Workstation - Question 6
15:31 - Workstation - Question 7
17:34 - Workstation -...
https://www.youtube.com/watch?v=A7Bh7vnAooQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Review: This Is How They Tell Me the World Ends (not with a bang but with a bug)
Join me on a brand-new series as I indulge my childhood dream of creating a personal library, focusing on InfoSec books! Kicking things off, we dive into 'This Is How They Tell Me How The World Ends' by Nicole Perlroth. Despite being an ebook enthusiast, I decided it was high time to fill my custom-built bookcase with real books. We'll explore the fascinating histories and personal stories behind bug bounties, zero days, and cyber warfare, all narrated with the flair of a seasoned journalist. From cyber politics to sassy hacker quips - what did happen to that salmon anyway? To how hackers take on the global stage of politics
00:00 Introduction to the Quest for Infosec Books
00:29 Building the Dream Library
00:55 E-Readers vs. Physical Books
02:41 Criteria for Book Selection
04:44 First Book...
https://www.youtube.com/watch?v=OvUmumbiGRI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Understanding the Bugcrowd VRT: An Insider's Guide
Join us at DEF CON as we sit down with Codingo, VP of Operations at Bugcrowd, to look into the Vulnerability Rating Taxonomy (VRT). Learn what makes the VRT unique, how it compares to other vulnerability rating systems like CVSS, and why it's a key part of Bugcrowd's platform. Discover how the VRT evolves, the community's role in its development, and essential tips for hackers advocating for higher priorities on their findings. Whether you're a seasoned Bugcrowd hacker or new to the platform, this interview offers valuable insights and practical advice for improving your skills and understanding of the VRT.
00:00 Introduction to the VRT and Bugcrowd
00:33 Bugcrowd's Unique Offerings for Hackers
01:19 Understanding the VRT: An Interview with Kodinga
02:22 Differences Between VRT and CVSS
03:09...
https://www.youtube.com/watch?v=AIJK_Lw8rKw
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Google's Mobile VRP Behind the Scenes with Kristoffer Blasiak (Hextree Podcast Ep.1)
"There are not that many people that do Android research [...] There is no lack of targets. If people would actually look, there is lots to it. The scope is huge." - This is a conversation with Kristoffer Blasiak about Google's Mobile Vulnerability Rewards Program (VRP).
Learn Android Hacking (ad): https://hextree.io/hextree-x-google
Mobile VRP: https://bughunters.google.com/about/rules/android-friends/6618732618186752/google-mobile-vulnerability-reward-program-rules
00:00 - Introducing Kristoffer and Mobile VRP
01:38 - What happens when you submit a bug
05:07 - Android app bug bounty opportunities
08:38 - "There is no lack of targets"
13:06 - The side-loading threat model
17:00 - Bugs in Android app vs. web app
23:30 - Hextree sponsored by Google
=[ ❤️ Support ]=
→ per Video:...
https://www.youtube.com/watch?v=SyTy1uZgx8E
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Reverse Engineering LAB Setup Tutorial (updated)
If you are just getting started with reverse engineering this the place to start. In this tutorial we provide an overview the current setup that we currently run, this is also the same setup used in all of our live streams and tutorials.
The full notes for this tutorial are unlocked for everyone on our Patreon including links to all of the tools mentioned
https://www.patreon.com/posts/101718688
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=adAr0KBJm4U
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Get Bigger Bounties With Better Reports
At DEFCON a few weeks ago, I sat down with Codingo, VP of operations to talk about the key elements of writing an effective bug report, especially for non-native English speakers and beginners. We also discuss the importance of clarity, accurate replication steps, and the impact of comprehensive report writing on your bug bounty success. Learn from Bugcrowd's framework and community-driven practices to enhance your cybersecurity skills and make a stronger impact with your findings.
00:00 Introduction and Apology
00:37 Sponsor Message: Bugcrowd
01:22 Live from DEF CON
01:53 The Importance of Report Writing
02:17 Key Elements of a Good Report
04:46 Challenges in Report Writing
06:11 The Triage Process
08:21 Support for Non-Native English Speakers
09:17 Common Reasons for Bug Rejection
11:09...
https://www.youtube.com/watch?v=hnU0mRl0WBI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
My theory on how the webp 0day was discovered (BLASTPASS)
Want to learn more about hacking? Checkout our courses on https://www.hextree.io (ad)
I have spent many hours looking at the webp vulnerability used in the 0day attack against iPhones. In the past videos we have seen why fuzzers have a hard time finding the issue, so I wanted to understand how this was discovered. And I think I have a good theory!
Part 1: Huffman Tables https://youtu.be/lAyhKaclsPM
Part 2: Fuzzing libwebp https://youtu.be/PJLWlmp8CDM
Sources:
https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/
https://googleprojectzero.blogspot.com/2019/08/the-fully-remote-attack-surface-of.html
https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-1.html
https://googleprojectzero.blogspot.com/2021/01/a-look-at-imessage-in-ios-14.html
https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js
https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html
https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/
https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html
https://github.com/libjxl/libjxl/blob/4b9dbde293f7f282b6952a02340300abfca2b184/lib/jxl/huffman_table.cc#L51
https://github.com/webmproject/libwebp/blob/7861947813b7ea02198f5d0b46afa5d987b797ae/src/dec/vp8l_dec.c#L86C3-L86C76
https://github.com/Tencent/mars/blob/9ab46e19ed3d4fcafe9d0de4b36547321f5ead83/mars/comm/windows/zlib/inftrees.h#L41
https://github.com/google/brunsli/blob/master/c/enc/jpeg_huffman_decode.h#L20
00:00...
https://www.youtube.com/watch?v=_ACCK0AUQ8Q
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Learn Android Hacking! - University Nevada, Las Vegas (2024)
During DEF CON and Black Hat, Google invited me to give a talk about Android hacking to students as part of init.g at the University Nevada, Las Vegas. In this talk I share my "trick" how to get into Android hacking and reverse engineering, which can also be adapted to any other topic.
Learn android hacking (ad): https://app.hextree.io/map/android
Watch my Vegas Vlog: https://www.youtube.com/watch?v=bhQ6FF3fCdA
Article about the init.g event: https://www.unlv.edu/announcement/academics/google-sponsors-initgvegas-student-event-unlv-during-defcon
=[ ❤️ Support ]=
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
2nd Channel: https://www.youtube.com/LiveUnderflow
=[ 🐕 Social ]=
→ Twitter: https://twitter.com/LiveOverflow/
→...
https://www.youtube.com/watch?v=fPt6fJDjKKM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC32 - Red Team Village - Recap
Thank you to everyone who attended the village this year at DEF CON! Another huge thank you to our core team, sponsors, volunteers, goons, and DEF CON!
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=xjKxLoz0Dw4
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
My Trip to Las Vegas for DEFCON & Black Hat
My second time in Las Vegas for DEF CON and Black Hat. Lots has changed since I have been here 6 years ago. This trip was quite emotional for me and I am so grateful for the experience. Hope to meet you all again.
Learn hacking (ad): https://app.hextree.io/
Buy our Faultier (US): https://1bitsquared.com/collections/embedded-hardware/products/faultier
Google x Hextree Android Courses: https://www.hextree.io/hextree-x-google
Raspberry Pi Hacking Challenge: https://www.hextree.io/rp2350
Embedded System Village: https://embeddedvillage.org/
My previous DEF CON 26 (6 years ago) Vlog:
- https://youtu.be/B8saYocsI-U
- https://www.youtube.com/watch?v=RXgp4cDbiq4
=[ ❤️ Support ]=
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
2nd...
https://www.youtube.com/watch?v=bhQ6FF3fCdA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
DC32 - Red Team Village x Amazon
Thank you Amazon for being a platinum sponsor! For more information about Amazon, please visit https://amazon.com.
Red Team Village Website: https://redteamvillage.io
Discord: https://redteamvillage.io/discord
Twitter: https://redteamvillage.io/twitter
https://www.youtube.com/watch?v=ouv0tgFmo8M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Planning Red Team Operations | Scope, ROE & Reporting
Hey guys, HackerSploit here back again with another video. This video outlines the process of planning and orchestrating Red Team operations.
This video also outlines various Red Team resources, guides, and templates to plan and orchestrate a successful Red Team Operation.
//LINKS & RESOURCES
REDTEAM.GUIDE: https://redteam.guide/
The slides and written version of this video can be accessed on the HackerSploit Forum: https://forum.hackersploit.org/t/introduction-to-the-mitre-att-ck-framework/9127
//HACKERSPLOIT PLATFORMS
BLOG ►► https://bit.ly/3qjvSjK
FORUM ►► https://bit.ly/39r2kcY
ACADEMY ►► https://bit.ly/39CuORr
//SOCIAL NETWORKS
TWITTER ►► https://bit.ly/3sNKXfq
INSTAGRAM ►► https://bit.ly/3sP1Syh
LINKEDIN ►► https://bit.ly/360qwlN
PATREON ►► https://bit.ly/365iDLK
MERCHANDISE...
https://www.youtube.com/watch?v=usDt-s2sACI
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Mapping APT TTPs With MITRE ATT&CK Navigator
Hey guys, HackerSploit here back again with another video. This video will introduce you to the MITRE ATT&CK Navigator and will illustrate how it can be operationalized for planning and orchestrating Red Team operations.
MITRE ATT&CK Framework: https://attack.mitre.org/
MITRE ATT&CK Navigator: https://mitre-attack.github.io/attack-navigator/
//PLATFORMS
BLOG ►► https://bit.ly/3qjvSjK
FORUM ►► https://bit.ly/39r2kcY
ACADEMY ►► https://bit.ly/39CuORr
//SOCIAL NETWORKS
TWITTER ►► https://bit.ly/3sNKXfq
DISCORD ►► https://bit.ly/3hkIDsK
INSTAGRAM ►► https://bit.ly/3sP1Syh
LINKEDIN ►► https://bit.ly/360qwlN
PATREON ►► https://bit.ly/365iDLK
MERCHANDISE ►► https://bit.ly/3c2jDEn
//BOOKS
Privilege Escalation Techniques ►► https://amzn.to/3ylCl33
Docker...
https://www.youtube.com/watch?v=hN_r3JW6xsY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Zombieware
Self-replicating malware, long abandoned by its operators, continues to contribute significant volume and noise to malware feeds. We investigate this trend, which we refer to as Zombieware!
Join us on Patreon for Part 2 where we reverse engineer a popular file infector and write an extractor to recover the infected files!
https://www.patreon.com/posts/zombieware-part-103656376
Full Zombieware blog post can be found on our UnpacMe blog here: https://blog.unpac.me/2024/04/25/zombieware/
Ladislav Zezula's excellent talk from BSides Prague can be found here:
https://www.youtube.com/watch?v=OgXvd-Wce9o
-----
OALABS DISCORD
https://discord.gg/oalabs
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED...
https://www.youtube.com/watch?v=NNLZmB6_aGA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Should I report this vulnerability? Will I get a bounty?
It's really exciting to find your first bug BUT it's crushing when you realise it isn't reportable or comes back as NA from a client. Here are my top tips for identifying if you've found something and double checking before getting caught up in excitement! I still get emails about IDORs being NA because you need a victims cookie and hackers who are angry at bug bounty programs or triagers.
https://www.youtube.com/watch?v=T4EhE5f7fQg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How to take notes when you suck at it
This episode of the Bug Bounty course we talk about the importance of developing a personal note taking system that supports both hacking and learning. Emphasizing the differentiation between notes taken during hacking activities and those for learning about vulnerabilities. We look at methods for organizing and accessing your notes whether you are into Notion, Obsidian or Vim or even mind maps we'll look at how to integrate your notes with tools like Burp Suite. Creating your own knowledge base you can refer to every time you hack, tailored to individual needs and preferences and refine your own note-taking strategies for successful hacking and learning.
00:00 Introduction to the Bug Bounty Course
00:14 The Importance of a Personalized Note-Taking System
00:53 Sponsor Shoutout: Bugcrowd
01:45...
https://www.youtube.com/watch?v=uXuMvUPlvd0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Finding The .webp Vulnerability in 8s (Fuzzing with AFL++)
A guide on how to do fuzzing with AFL++ in an attempt to rediscover the libwebp vulnerability CVE-2023-4863 that was used to hack iPhones.
Want to learn hacking? Signup to https://hextree.io (ad)
Buy my shitty font: https://shop.liveoverflow.com/ (ad)
Watch webp Part 1: https://www.youtube.com/watch?v=lAyhKaclsPM
Sudo Vulnerability Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjy0gMuT4C3bmjeZjuNQyqdx
Docker Video: https://www.youtube.com/watch?v=-YnMr1lj4Z8
OSS-Fuzz: https://github.com/google/oss-fuzz
OSS-Fuzz libwebp coverage: https://storage.googleapis.com/oss-fuzz-coverage/libwebp/reports/20230901/linux/src/libwebp/src/utils/report.html
AFLplusplus: https://github.com/AFLplusplus/AFLplusplus/blob/stable/docs/fuzzing_in_depth.md
vanhauser's blog: https://www.srlabs.de/blog-post/advanced-fuzzing-unmasks-elusive-vulnerabilities
vanhauser/thc...
https://www.youtube.com/watch?v=PJLWlmp8CDM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction to YARA Part 4 - Efficient Rule Development
In this OALABS Patreon tutorial we cover the foundations of writing efficient YARA rules and provide some tips that can help speed up your YARA hunting.
The full notes for this tutorial are unlocked for everyone on our Patreon
https://www.patreon.com/posts/introduction-to-96638239
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=xKeF_cPKXt0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction to YARA Part 3 - Rule Use Cases
In this OALABS Patreon tutorial we cover the three main use cases for YARA rules and how they apply to both BlueTeam/SOC operations and malware analysis.
Fun notes have been unlocked for everyone on our Patreon here
https://www.patreon.com/posts/introduction-to-96637668
The following are links to UnpacMe specific tutorials for developing each type of rule.
Identifying specific malware families (unpacked)
https://support.unpac.me/howto/hunting-with-yara/#identifying-specific-malware-families-unpacked
Identifying malware on disk or in network traffic (packed)
https://support.unpac.me/howto/hunting-with-yara/#identifying-malware-on-disk-or-in-network-traffic-packed
Hunting (malware characteristics)
https://support.unpac.me/howto/hunting-with-yara/#hunting-malware-characteristics
-----
OALABS...
https://www.youtube.com/watch?v=xutDqu_OiH8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction to YARA Part 2 - Hunting on UnpacMe
In this OALABS Patreon tutorial we demonstrate a simple YARA hunting example using the UnpacMe free YARA scan service: https://www.unpac.me
Full notes have been unlocked on our Patreon here
https://www.patreon.com/posts/introduction-to-96637337
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=Xqvlju9ED1c
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Introduction to YARA Part 1 - What is a YARA Rule
In this OALABS Patreon tutorial we cover the basics of YARA, what is it, how is it used, and how to write your first rule.
Full notes have been unlocked on our Patreon here
https://www.patreon.com/posts/introduction-to-96636471
-----
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
OALABS PATREON
https://www.patreon.com/oalabs
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=3BpIhbsDR_I
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Approaching Large Scope Targets Without Feeling Overwhelmed
In this video, we discuss how beginners can tackle large scope targets in bug bounty hunting. These targets offer more flexibility and potential for bug discovery, making them a great starting point for new hackers. However, they can be overwhelming due to their size and diversity. We suggest focusing on one part of the larger scope, which helps you understand the target's application development process without becoming overwhelmed. We also delve into different reconnaissance techniques, including subdomain enumeration, Google Dorking, API enumeration, OSINT, and more. Lastly, we emphasize that while reconnaissance is critical for large scope targets, it is just a stepping stone to actually hacking and finding vulnerabilities.
This series couldn't happen without the support of our sponsor...
https://www.youtube.com/watch?v=W4pafFxOOwc
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
OALABS Holiday Variety Show 2023
𝘔𝘦𝘳𝘳𝘺 𝘐𝘋𝘈𝘮𝘢𝘴 𝘢𝘯𝘥 𝘢 𝘏𝘢𝘱𝘱𝘺 𝘉𝘪𝘯𝘫𝘢-𝘠𝘦𝘢𝘳
Join us for our holiday special reverse engineering variety show!
- Guess the prompt AI charades
- Random RE banter
- Suspicious liquids in bottles
We've got it all!
Merry Christmas everyone we will see you in 2024!
-----
OALABS PATREON
https://www.patreon.com/oalabs
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=XMVhX29AJbQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
A Vulnerability to Hack The World - CVE-2023-4863
Citizenlab discovered BLASTPASS, a 0day being actively exploited in the image format WebP. Known as CVE-2023-4863 and CVE-2023-41064, an issue in webp's build huffman table function can lead to a heap buffer overflow. This vulnerability is very interesting and I'm excited to share with you what I learned.
Want to learn hacking? Signup to https://hextree.io (ad)
Buy my shitty font: https://shop.liveoverflow.com/ (ad)
WebP Fix Commit: https://chromium.googlesource.com/webm/libwebp/+/902bc9190331343b2017211debcec8d2ab87e17a
Citizenlab: https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/
Ben Hawkes: https://blog.isosceles.com/the-webp-0day/
Software Updates
Apple https://support.apple.com/en-gb/106361
Chrome https://chromereleases.googleblog.com/2023/09/stable-channel-update-for-desktop_11.html
Firefox...
https://www.youtube.com/watch?v=lAyhKaclsPM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Tips For Analyzing Delphi Binaries in IDA (Danabot)
Reverse Engineering Delphi is a nightmare ... or it can be if you don't have the right setup! In this clip we cover some easy tips that can help make some of the analysis a bit easier.
Full notes with links for tools are available here:
https://research.openanalysis.net/danabot/loader/delphi/2023/12/04/danabot.html
Full stream with analysis of the Danabot loader is available on Patreon here:
https://www.patreon.com/posts/live-stream-vod-94510766
-----
OALABS PATREON
https://www.patreon.com/oalabs
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=04RsqP_P9Ss
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
How To Recognize Macro Encrypted Strings in Malware
How to identify when a macro is used to encrypt strings in malware... inferring source from disassembly!
-----
OALABS PATREON
https://www.patreon.com/oalabs
OALABS DISCORD
https://discord.gg/6h5Bh5AMDU
Twitch
https://www.twitch.tv/oalabslive
OALABS GITHUB
https://github.com/OALabs
UNPACME - AUTOMATED MALWARE UNPACKING
https://www.unpac.me/#/
-----
https://www.youtube.com/watch?v=fEAGYjhKzJY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Reinventing Web Security
Follow me down the rabbit hole into the wonderful world of IT security.
Buy my terrible font (ad): https://shop.liveoverflow.com
Learn hacking (ad): https://hextree.io
Related Videos:
https://www.youtube.com/watch?v=866olNIzbrk
https://www.youtube.com/watch?v=lKzsNp4AveY
Tweets:
https://twitter.com/LiveOverflow/status/1720734431659376995
https://twitter.com/LiveOverflow/status/1720799912181284864
https://twitter.com/LiveOverflow/status/1721493232310214910
Understanding the Risks of Stolen Credentials: https://static.googleusercontent.com/media/research.google.com/en//pubs/archive/46437.pdf
Chapters:
00:00 - Intro
00:40 - Security Terminology
01:38 - Direct Database Access
03:40 - Introducing a Security Boundary
05:36 - Typical Web Security Vulnerabilities
07:03 - Clear-text Passwords...
https://www.youtube.com/watch?v=LxUAnZY_08o
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The Circle of Unfixable Security Issues
Not every security issues can be fixed. There exist (what I call) "unfixable" bugs, where you can always argue and shift the goal posts. The idea is to only report these kind of issues to create an endless stream of bug bounty money!
Buy my terrible font (ad): https://shop.liveoverflow.com
Learn hacking (ad): https://hextree.io
What is a vulnerability? https://www.youtube.com/watch?v=866olNIzbrk
hackerone reports:
https://hackerone.com/reports/812754
https://hackerone.com/reports/6883
https://hackerone.com/reports/223337
https://hackerone.com/reports/819930
https://hackerone.com/reports/224460
https://hackerone.com/reports/160109
https://hackerone.com/reports/557154
OWASP: https://owasp.org/www-community/controls/Blocking_Brute_Force_Attacks
Chapters:
00:00 - Intro
00:30 - Denial of Service...
https://www.youtube.com/watch?v=lr1KuL8OmJY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hacker Tweets Explained
Let me explain to you what you can learn from these tweets. Did you know the name trick?
Buy my terrible font (ad): https://shop.liveoverflow.com
Learn hacking (ad): https://hextree.io
Quote Tweet: https://twitter.com/avlidienbrunn/status/1697869590569582932
Original Tweet: https://twitter.com/Rhynorater/status/1696862832841916679
Critical Thinking Podcast: https://www.criticalthinkingpodcast.io/
XSS Origin Series: https://www.youtube.com/playlist?list=PLhixgUqwRTjyakFK7puB3fHVfXMinqMSi
Chapters:
00:00 - Intro
00:37 - Tweets About Tricky XSS
01:24 - XSS Testbed Setup with php
03:45 - Exploring the XSS Context
05:24 - The window Object
06:46 - Tweet 1: Justin's XSS Explained
08:22 - Tweet 2: Mathias's Variant With Object
09:52 - Tweet 2: Mathias's Variant Creating Class
10:30 - The window.name...
https://www.youtube.com/watch?v=3zShGLEqDn8
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
401 Access Denied Ep88: The RISE of the CISO with Merike Kaeo
This week Joe Carson is joined by Merike Kaeo as they discuss the dynamic role of the CISO within an organization. They dive deeper into the role and how it interacts with different areas of the business, and what specific assets need protection and within what frameworks. An episode not to be missed!
Jump-start your cybersecurity career for FREE with Cybrary!
Follow us on Social!
~Cybrary Twitter
~Delinea Twitter
~Instagram
~Facebook
~YouTube
https://www.youtube.com/watch?v=FklaFGnBEyQ
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Zenbleed (CVE-2023-20593)
Let's explore the "most exciting" CPU vulnerability affecting Zen2 CPUs from AMD.
Watch part 1 about fuzzing: https://www.youtube.com/watch?v=neWc0H1k2Lc
buy my font (advertisement): https://shop.liveoverflow.com/
This video is sponsored by Google: https://security.googleblog.com/2023/08/downfall-and-zenbleed-googlers-helping.html
Original Zenbleed Writeup: https://lock.cmpxchg8b.com/zenbleed.html
Grab the code: https://github.com/google/security-research/tree/master/pocs/cpus/zenbleed
cvtsi2ss: https://www.felixcloutier.com/x86/cvtsi2ss.html
AMD Security Bulletin: https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7008.html
RIDL Video: https://www.youtube.com/watch?v=x_R1DeZxGc0
Tavis Ormandy: https://twitter.com/taviso
Chapters:
00:00 - Intro
02:27 - zenleak.asm Patterns
03:56...
https://www.youtube.com/watch?v=9EY_9KtxyPg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Intruder Alert Ep. 6 | Deconstructing Malware Attacks & Forging a Career in Cybersecurity
In this episode of Intruder Alert, Marcus Hutchins is joined by cybersecurity expert Caitlin Sarian, known for her role as the Global Lead of Cybersecurity Advocacy and Culture at TikTok and her expertise in data protection and privacy compliance. Marcus and Caitlin provide technical insight into the latest US malware attacks and share invaluable advice on breaking into the cybersecurity field.
Follow us on Social!!
~Twitter
~Instagram
~FaceBook
~YouTube
~LinkedIn
Jump-start your cybersecurity career for FREE with Cybrary!
https://www.youtube.com/watch?v=2aRgdmTdtK0
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
401 Access Denied: Protecting Society and the Role of CERT with Tonu
In this episode we join host Joe Carson as he discusses state cybersecurity with Tonu Tammer of the Estonian National Cybersecurity Center. Tonu goes into the day-to-day operations of defending a country and its citizens from adversaries, as well as ransomware and DDOS attacks. Come along for an in-depth discussion with a cyber defender with years of experience in this exciting new episode!
Jump-start your cybersecurity career for FREE with Cybrary!
Follow us on Social!
~Cybrary Twitter
~Delinea Twitter
~Instagram
~Facebook
~YouTube
https://www.youtube.com/watch?v=aYCyFDlK7vg
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Intruder Alert Ep. 5 | Community Uprising: Unravelling the Reddit Blackout
In the latest episode of Intruder Alert, Marcus Hutchins and Cybrary blue teamer, Marc Balingit, delve into the the uproar around Reddit's blackout. They unravel the intricacies of Reddit's contentious API changes, which have cornered third-party apps like Apollo, sparking a sweeping blackout protest across thousands of subreddits. Furthermore, they explore the impact of Twitch's fresh policy adjustments, which are a threat to streamers' ad revenue, and other news impacting online communities.
Follow us on Social!!
~Twitter
~Instagram
~FaceBook
~YouTube
~LinkedIn
Jump-start your cybersecurity career for FREE with Cybrary!
https://www.youtube.com/watch?v=8_CEqpKU8AA
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
401 Access Denied: Ep. 85 | Key Takeaways from the Verizon DBIR with Tony Goulding
Join host Joseph Carson and guest Tony Goulding as they break down the annual Verizon breach report. With over 16,000 incidents and more than 5,200 data breaches, there's a lot to look at. Tony and Joe have some great takeaways from this critical annual report and share their expert insights on what's new, what's changed, and what we're not doing so bad at (hint: MFA goes a long way!)
Jump-start your cybersecurity career for FREE with Cybrary!
Follow us on Social!
~Cybrary Twitter
~Delinea Twitter
~Instagram
~Facebook
~YouTube
https://www.youtube.com/watch?v=luXnfWO_U7I
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
401 Access Denied: Ep. 84 | The Best of RSAC & Cybersecurity Strategies with Bob Burns
RSAC was the place to be for cybersecurity in 2023, and Joe Carson is joined by Bob Burns to talk all about it. From the sessions that really resonated to the incredible human connections and networking, join Joe and Bob to deconstruct this year's most comprehensive conference. Were you at RSAC this year? Join us in the comments to let us know your favorite session!
Jump-start your cybersecurity career for FREE with Cybrary!
Follow us on Social!
~Cybrary Twitter
~Delinea Twitter
~Instagram
~Facebook
~YouTube
https://www.youtube.com/watch?v=qU40Yg7pfbo
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
The AI Revolution with Diana Kelley | 401 Access Denied Podcast Ep. 83
The AI Revolution with Diana Kelley | 401 Access Denied Podcast Ep. 83
Join Us: https://www.cybrary.it/?utm_source=youtube&utm_medium=video&utm_campaign=the-ai-revolution-with-diana-kelley
Everybody's talking about it - the AI revolution is here. But given the rapid evolution in this field, it's hard to keep up with the sweeping effects this technology is causing. Luckily, Joe Carson is joined by longtime AI expert Diana Kelley to shed light on all of these changes. She addresses the many misconceptions and media misrepresentations surrounding AI, breaks down the different forms of this technology, and emphasizes the need for a better understanding of AI's capabilities and limitations. They also discuss the ethical and legal implications that will only become more potent as AI...
https://www.youtube.com/watch?v=ow9JszgoC1M
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Hacking the Government with Bryan Seely | 401 Access Denied Podcast Ep. 82
Hacking the Government with Bryan Seely | 401 Access Denied Podcast Ep. 82
Join Us: https://www.cybrary.it/?utm_source=youtube&utm_medium=video&utm_campaign=hacking-the-government-with-bryan-seely
In this eye-opening episode, dive into the captivating world of cybercrime and social engineering with our host, Joe Carson, and special guest Bryan Seely! Bryan, a keynote speaker and cybersecurity expert best known for his Secret Service exposé, discusses his journey from a young computer enthusiast to a renowned public speaker. Join them as they investigate the mindset and techniques used by hackers, such as the use of aliases to deceive and manipulate their targets, as well as the importance of responsible disclosure and changing cybersecurity laws.
Follow us for exclusive updates:
~https://twitter.com/cybraryIT
~https://www.instagram.com/cybrary.it/
~https://www.facebook.com/cybraryit/
Follow...
https://www.youtube.com/watch?v=aagD2SxYUJM
Partager : LinkedIn / Twitter / Facebook / View / View (lite)
Intruder Alert Ep. 4 | Unmasking The New Global Malware Threat On Android Devices
Head to Cybrary.it to open your free account and start learning today!
In this episode of Intruder Alert, join host Marcus Hutchins, world-renowned hacker, and red teamer Matt Mullins while they discuss the millions of devices recently infected with malware during production, and whether or not our devices are spying on us.
For more information on how to jumpstart your career with the most cutting-edge cybersecurity training, head over to Cybrary.it to create your free account and get started on your learning journey!
Make sure to subscribe so that you don't miss the latest new episodes, premiering live every two weeks, and dropping on YouTube On Demand.
https://www.youtube.com/watch?v=wc8T_RcwOkY
Partager : LinkedIn / Twitter / Facebook / View / View (lite)